 |
市場調查報告書
商品編碼
1589862
IoT網路安全的全球市場:2024-2029年Global IoT Cybersecurity Market: 2024-2029 |
||||||
"到 2029 年,全球物聯網網路安全市場規模預計將達到 600 億美元"
| 主要統計 | |
|---|---|
| 2024年的總收益: | 270億磅 |
| 2029年的總收益: | 600億美元 |
| 2021~2029年的市場成長率: | 124% |
| 預測期間: | 2024-2029年 |
該研究套件對不斷發展的物聯網網路安全市場進行了詳細而深入的研究,以幫助包括物聯網網路安全服務提供者、監管機構和製造商在內的利益相關者了解未來的成長、主要趨勢和競爭格局。它還包括產品和服務分析,分析物聯網網路安全關鍵領域的當前趨勢和重要的貨幣化機會,包括網路安全、平台安全、端點安全和應用程式安全。
該研究套件包括對數據的訪問,這些數據映射了未來五年物聯網網路安全服務的採用和未來增長,以及關鍵的物聯網網路安全部分(網路安全、平台安全、端點安全、應用程序安全,包含多個選項,可單獨購買,例如按安全性分段的資料、其他安全解決方案)。
我們也提供了一項富有洞察力的研究,揭示了物聯網網路安全市場的最新趨勢和機遇,例如區塊鏈在網路安全中的使用,以及對物聯網17 個市場領導者的廣泛分析網路安全空間我正在做。
主要特點:
- 主要要點和策略建議:詳細分析物聯網網路安全市場的主要成長機會和見解,並為物聯網網路安全供應商、原始設備製造商(OEM) 和監管機構提供戰略建議。
- 市場展望:深入了解物聯網網路安全市場的主要趨勢和市場擴張挑戰,解決有限的網路安全預算和物聯網網路複雜性所帶來的挑戰。為物聯網網路安全服務供應商、製造商和監管機構提供建議並發現關鍵的獲利機會,以克服當前的市場挑戰。它還分析了市場成長的關鍵推動因素,例如物聯網採用的快速成長、監管環境的加強以及網路攻擊的增加。
- 產業預測基準:提供物聯網網路安全市場規模和預測,包括總收入、採用物聯網網路安全的公司總數以及受物聯網網路安全保護的物聯網設備總數。該預測進一步將總收入和企業部署細分為以下部分:網路安全、平台安全、端點安全、應用程式安全和其他物聯網網路安全解決方案。
- Juniper Research 競爭排行榜:透過 Juniper Research 的競爭排行榜評估 17 家 IoT 網路安全供應商的能力。
樣品view
市場資料·預測報告
市場趨勢·策略報告
市場資料&預測報告
該研究套件包括對 40 個表格和 18,200 多個數據點中的全套預測數據的存取。此調查套件包括以下指標:
- IoT的整體引進數
- 採用IoT網路安全解決方案的企業的總數
- IoT網路安全的總收益
這些的指標,以下的主要各市場被提供的:
- 應用保全
- 終端安全
- 網路安全
- 平台保全
- 其他
瞻博網路研究互動式預測 (Excel) 具有以下功能:
- 統計分析:您可以搜尋資料期間為所有地區和國家顯示的特定指標。可以輕鬆修改圖表並將其匯出到剪貼簿。
- 國家/地區資料工具:此工具可讓您查看預測期間內的所有區域和國家指標。您可以縮小搜尋列中顯示的指標範圍。
- 國家比較工具:您可以選擇特定國家進行比較。該工具包括匯出圖表的功能。
- 假設分析:五種互動式場景讓使用者比較預測假設。
目錄
市場趨勢·策略
第1章 重要點·策略性推薦事項
- 重要點
- 策略性推薦事項
第2章 未來市場展望:促進因素·課題
- 電腦網路威脅
- IoT網路安全解決方案
- 推動市場要素
- 擴大的IoT引進
- 攻擊的增加
- 國家的法規和法律
- 課題
- 物聯網網路的複雜性
- 缺乏合法認證
- 網路安全預算
- 缺乏教育
第3章 市場趨勢
- 零信任架構
- AI與機器學習
- 邊緣運算
- 量子通訊和後量子密碼
- 區塊鏈
- OTA更新
第4章 產品及服務的分析
- 網路安全
- 平台保全
- 應用保全
- 終端安全
- 資安管理服務
- 專業保全服務
競爭排行榜
第1章 Juniper Research的競爭排行榜
第2章 企業簡介
- IoT網路安全-業者簡介
- Armis
- AWS
- Broadcom
- Cisco
- Claroty
- Entrust
- Forescout
- Fortinet
- Honeywell
- IBM
- Intel
- Microsoft
- Palo Alto Networks
- Ping Identity
- Rapid7
- Thales
- Trend Micro
- 排行榜評估手法
資料·預測
第1章 IoT網路安全:預測·重要點
- IoT網路安全市場概要和未來展望
- 預測手法
第2章 全球IoT網路安全市場
- IoT網路安全解決方案的引進企業總數
- IoT網路安全的總收益
第3章 網路安全
- 網路安全的總收益
- 網路安全硬體設備的總成本
第4章 終端安全
- 終端安全被保護的IoT設備的總數
- 終端安全的總收益
第5章 平台保全
- 平台保全的總收益
- 平台保全的引進企業數
第6章 應用保全
- 應用保全
- 應用保全的引進企業數
第7章 其他的保全解決方案
- 其他的保全解決方案的收益
- 其他的保全解決方案硬體設備的總成本
'IoT Cybersecurity Market to Reach $60 Billion Globally by 2029'
| KEY STATISTICS | |
|---|---|
| Total revenue in 2024: | Pound-27bn |
| Total revenue in 2029: | $60bn |
| 2021 to 2029 market growth: | 124% |
| Forecast period: | 2024-2029 |
Overview
Juniper Research's "IoT Cybersecurity" research suite provides a detailed and insightful analysis of this evolving market; enabling stakeholders including IoT cybersecurity service providers, regulators, and manufacturers to understand future growth, key trends, and the competitive environment. Additionally, it includes a product and service analysis that studies the current trends and critical monetisation opportunities of the key segments of IoT cybersecurity including network security, platform security, endpoint security and application security. The coverage can also be purchased as a full research suite, containing all of these elements, at a substantial discount.
The research suite includes several different options that can be purchased separately, including access to data mapping the adoption and future growth of IoT cybersecurity service over the next five years, split by the key IoT cybersecurity segments: network security, platform security, endpoint security, application security, and other security solutions.
It also provides an insightful study uncovering the latest trends and opportunities within the IoT cybersecurity market, such as the use of blockchain in cybersecurity, and a document containing an extensive analysis of the 17 market leaders in the IoT cybersecurity space.
Collectively, these documents provide a critical tool for understanding this fast-evolving market, allowing IoT cybersecurity providers and manufacturers to shape their future strategy and capitalise on future growth opportunities in digitally transforming regions. Its extensive coverage makes this research suite a valuable tool for navigating this rapidly growing market in the midst of an increasing regulatory landscape.
Key Features
- Key Takeaways & Strategic Recommendations: In-depth analysis of key development opportunities and findings within the IoT cybersecurity market, accompanied by strategic recommendations for IoT cybersecurity vendors, OEMs, and regulators.
- Market Outlook: Insights into critical trends and market expansion challenges within the IoT cybersecurity market; addressing those posed by limited cybersecurity budgets and IoT network complexity. It provides recommendations for IoT cybersecurity service providers, manufacturers, and regulators to overcome the current market challenges and highlights key monetisation opportunities. It also analyses the main drivers behind market growth, including the rapid growth of IoT deployments, increasing regulatory landscapes, and the growing number of cyber-attacks.
- Benchmark Industry Forecasts: The market size and forecast for IoT cybersecurity including total revenue, total businesses adopting IoT cybersecurity, and total number of IoT devices protected by IoT cybersecurity. The forecast further breaks down total revenue and business adoption into the following segments: network security, platform security, endpoint security, application security, and other IoT cybersecurity solutions.
- Juniper Research Competitor Leaderboard: Key player capability and capacity assessment for 17 IoT cybersecurity vendors, via the Juniper Research Competitor Leaderboard, featuring IoT cybersecurity market size for major players in the IoT cybersecurity industry.
SAMPLE VIEW
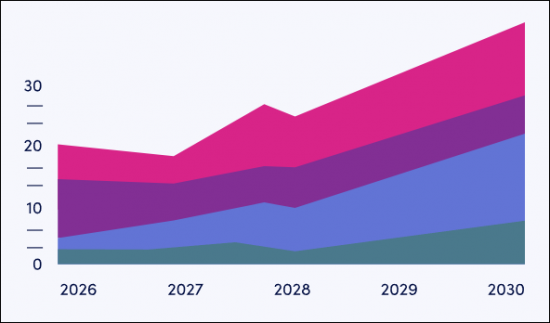
Market Data & Forecasting Report

The numbers tell you what's happening, but our written report details why, alongside the methodologies.
Market Trends & Strategies Report

A comprehensive analysis of the current market landscape, alongside strategic recommendations.
Market Data & Forecasting Report
The market-leading research suite for the "IoT Cybersecurity" market includes access to the full set of forecast data of 40 tables and over 18,200 datapoints. Metrics in the research suite include:
- Total Number of IoT Deployments
- Total Number of Businesses Adopting IoT Cybersecurity Solutions
- Total IoT Cybersecurity Revenue
These metrics are provided for the following key market verticals:
- Application Security
- Endpoint Security
- Network Security
- Platform Security
- Other
Juniper Research Interactive Forecast Excel contains the following functionality:
- Statistics Analysis: Users benefit from the ability to search for specific metrics, displayed for all regions and countries across the data period. Graphs are easily modified and can be exported to the clipboard.
- Country Data Tool: This tool lets users look at metrics for all regions and countries in the forecast period. Users can refine the metrics displayed via a search bar.
- Country Comparison Tool: Users can select and compare specific countries. The ability to export graphs is included in this tool.
- What-if Analysis: Here, users can compare forecast metrics against their own assumptions, via five interactive scenarios.
Market Trends & Strategies Report
This report examines the "IoT Cybersecurity" market landscape in detail; assessing market trends and factors shaping the evolution of this rapidly growing market. As IoT deployments continue to rise globally, cyber-attacks are increasing in volume and sophistication; driving market trends such as AI-and blockchain adoption in IoT cybersecurity solutions and services. However, IoT network complexity and low cybersecurity budgets restrain the market from full growth.
This report delivers a comprehensive analysis of the strategic opportunities for IoT cybersecurity service providers and manufacturers; analysing developing challenges and highlighting opportunities in key industries as well as assessing how stakeholders should navigate these. It also includes an evaluation of key segment opportunities for IoT cybersecurity services operators, underlining markets with the highest potential for growth.
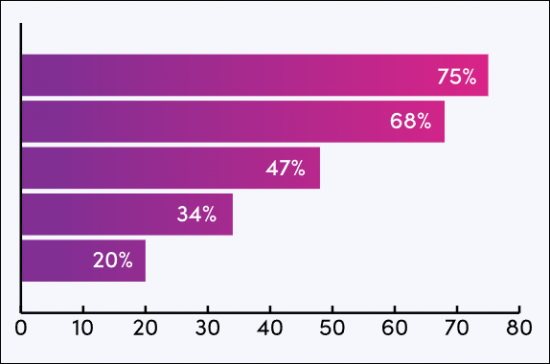
Competitor Leaderboard Report
The Competitor Leaderboard report provides a detailed evaluation and market positioning for 17 leading vendors in the IoT cybersecurity space. The vendors are positioned as an established leader, leading challenger or disruptor and challenger, based on capacity and capability assessments:
|
|
This document is centred on the Juniper Research Competitor Leaderboard; a vendor positioning tool that provides an at-a-glance view of the competitive landscape in a market, backed by a robust methodology.
Table of Contents
Market Trends & Strategies
1. Key Takeaways & Strategic Recommendations
- 1.1. Key Takeaways
- 1.2. Strategic Recommendations
2. Future Market Outlook: Drivers and Challenges
- 2.1. Introduction
- 2.2. Cyber Threats
- Table 2.1: Summary of Common Cyber Attacks, Split by Type
- 2.3. IoT Cybersecurity Solutions
- Figure 2.2: Total IoT Cybersecurity Revenue (m), 2024-2029, Split by Key Market Segments
- i. Network Security
- Figure 2.3: Total Revenue from Network Security (m) 2024-2029, Spilt by 8Key Regions
- ii. Application Security
- iii. Cloud Security
- iv. Endpoint Security
- Figure 2.4: Total Revenue from Endpoint Security (m) 2024-2029, Spilt by 8Key Regions
- Figure 2.5: Types of IoT Cybersecurity in an IoT Ecosystem
- 2.4. Market Drivers
- 2.4.1. Growing IoT Deployments
- Figure 2.6: Total IoT Deployment (m) 2024-2029, Split by 8Key Regions
- 2.4.2. Increased Attacks
- 2.4.3. National Regulations and Laws
- Figure 2.7: Summary of Key National Regulations
- Source: Juniper Research
- Figure 2.7: Summary of Key National Regulations
- 2.4.1. Growing IoT Deployments
- 2.5. Challenges
- 2.5.1. IoT Network Complexity
- 2.5.2. Lack of Legal Certifications
- 2.5.3. Cybersecurity Budgets
- 2.5.4. Lack of Education
3. Market Trends
- 3.1. Introduction
- 3.1.1. Zero Trust Architecture
- Figure 3.1: The Five Pillars of Zero Trust Architecture
- 3.1.2. AI and Machine Learning
- 3.1.3. Edge Computing
- 3.1.4. Quantum Communications and Post-Quantum Cryptography
- 3.1.5. Blockchain
- Figure 3.2: The Advantages of Blockchain for IoT Cybersecurity
- 3.1.6. OTA Updates
- 3.1.1. Zero Trust Architecture
4. Product and Service Analysis
- 4.1. Introduction
- 4.1.1. Network Security
- i. Future Market Landscape
- ii. Key Monetisation Opportunities
- 4.1.2. Platform Security
- i. Future Market Outlook
- ii. Key Monetisation Opportunities
- Figure 4.1: Total Number of Businesses Adopting Platform Security Solutions 2024-2029, Split By 8Key Regions
- 4.1.3. Application Security
- i. Future Market Outlook
- ii. Key Monetisation Opportunities
- Figure 4.2: Total Number of Businesses Adopting Application Security Solutions 2024-2029, Split By 8Key Regions
- 4.1.4. Endpoint Security
- i. Future Market Outlook
- ii. Key Monetisation Opportunities
- 4.1.5. Managed Security Services
- 4.1.6. Professional Security Services
- 4.1.1. Network Security
Competitor Leaderboard
1. Juniper Research Competitor Leaderboard
- 1.1. Why Read this Report?
- Table 1.1: Juniper Research Competitor Leaderboard: IoT Cybersecurity Providers: Product & Portfolio (Part 1)
- Source: Juniper Research
- Figure 1.2: Juniper Research Competitor Leaderboard: IoT Cybersecurity Providers
- Figure 1.3: Juniper Research Competitor Leaderboard: Vendor & Position
- Source: Juniper Research
- Table 1.5: Juniper Research Competitor Leaderboard Heatmap - IoT Cybersecurity Vendors
- Table 1.1: Juniper Research Competitor Leaderboard: IoT Cybersecurity Providers: Product & Portfolio (Part 1)
2. Company Profiles
- 2.1. IoT Cybersecurity - Vendor Profiles
- 2.1.1. Armis
- i. Corporate
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- Figure 2.1: Armis' Centrix Platform Ecosystem
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- 2.1.1. Armis
- 2.2. AWS
- i. Corporate
- Table 2.2: AWS Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- 2.2.2. Broadcom
- i. Corporate
- Table 2.3: Broadcom's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.3. Cisco
- i. Corporate
- Table 2.4: Cisco's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.4. Claroty
- i. Corporate
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- 2.2.5. Entrust
- i. Corporate
- Table 2.5: Entrust's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- Forescout
- i. Corporate
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- Figure 2.6: Summary of the Key Features of the Forescout Platform
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- 2.2.2. Fortinet
- i. Corporate
- Table 2.7: Fortinet's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.3. Honeywell
- i. Corporate
- Table 2.8: Honeywell's Financial Summary ($m), 2020-2022
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.4. IBM
- i. Corporate
- Table 2.9: IBM's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.5. Intel
- i. Corporate
- Table 2.10: Intel's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.6. Microsoft
- i. Corporate
- Table 2.11: Microsoft's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.7. Palo Alto Networks
- i. Corporate
- Table 2.12: Palo Alto Network's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.8. Ping Identity
- i. Corporate
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- 2.2.9. Rapid7
- i. Corporate
- Table 2.13: Rapid7's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- Figure 2.14: Summary of the Key Features of Rapid7's Command Platform
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.10. Thales
- i. Corporate
- Table 2.15: Thales' Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- Figure 2.16: Thales' Data Protection Services
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- 2.2.11. Trend Micro
- i. Corporate
- Table 2.17: Trend Micro's Financial Summary ($m), 2022-2023
- ii. Geographical Spread
- iii. Key Clients and Strategic Partnerships
- iv. High-level View of Offerings
- Figure 2.18: Summary of Trend Micro's Trend Vision One Platform features
- v. Juniper Research's View: Key Strengths and Strategic Development Opportunities
- i. Corporate
- i. Corporate
- 2.3. Juniper Research Leaderboard Assessment Methodology
- 2.3.1. Limitation & Interpretations
- Table 2.19: Juniper Research Competitor Leaderboard Scoring Criteria
- 2.3.1. Limitation & Interpretations
Data & Forecasting
1. IoT Cybersecurity Forecast and Key Takeaways
- 1.1. IoT Cybersecurity Market Summary & Future Outlook
- 1.2. Forecast Methodology
- Figure 1.1: Total Network Security IoT Cybersecurity Forecast Methodology
- Source: Juniper Research Figure 1.2: Total Endpoint Security IoT Cybersecurity Forecast Methodology
- Source: Juniper Research Figure 1.3: Total Platform Security IoT Cybersecurity Forecast Methodology
- Source: Juniper Research Figure 1.4: Total Application Security IoT Cybersecurity Forecast Methodology
- Source: Juniper Research Figure 1.5: Total Other Security Solutions IoT Cybersecurity Forecast Methodology
- Figure 1.1: Total Network Security IoT Cybersecurity Forecast Methodology
2. Global IoT Cybersecurity Market
- 2.1. Total Businesses Adopting IoT Cybersecurity Solutions
- Figure and Table 2.1: Total Number of Businesses Adopting IoT Cybersecurity Solutions (m), Split by 8Key Regions, 2024-2029
- 2.2. Total IoT Cybersecurity Revenue
- Figure and Table 2.2: Total IoT Cybersecurity Revenue (m), Split by 8Key Regions, 2024-2029
- Table 2.3: Total IoT Cybersecurity Revenue ($m), Split by Solution, 2024-2029
3. Network Security
- 3.1. Total Network Security Revenue
- Figure and Table 3.1: Total IoT Cybersecurity Revenue from Network Security (m), Split by 8Key Regions, 2024-2029
- 3.2. Total Network Security Hardware Cost
- Figure & Table 3.2: Total Network Security Hardware Cost per Annum (m), Split by 8Key Regions, 2024-2029
4. Endpoint Security
- 4.1. Total Number of IoT Devices Protected by Endpoint Security
- Figure and Table 4.1: Total Number of IoT Devices Protected by Endpoint Security Revenue (m), Split by 8Key Regions, 2024-2029
- 4.2. Total Endpoint Security Revenue
- Figure and Table 4.2: Total IoT Cybersecurity Revenue from Endpoint Security (m), Split by 8Key Regions, 2024-2029
- Table 4.3: Total Number of IoT Devices (m), Split by 8Key Regions, 2024-2029
5. Platform Security
- 5.1. Total Platform Security Revenue
- Figure and Table 5.1: Total IoT Cybersecurity Revenue from Platform Security (m), Split by 8Key Regions, 2024-2029
- 5.2. Total Number of Businesses Adopting Platform Security
- Figure 5.2: Total Number of Businesses Adopting Platform Security (m), Split by Key Regions, 2024-2029
6. Application Security
- 6.1. Application Security
- Figure and Table 6.1: Total IoT Cybersecurity Revenue from Application Security (m), Split by 8Key Regions, 2024-2029
- 6.2. Total Number of Businesses Adopting Application Security
- Figure and Table 6.2: Total Number of Businesses Adopting Application Security (m), Split by 8Key Regions, 2024-2029
7. Other Security Solutions
- 7.1. Other Security Solutions Revenue
- Figure and Table 7.1: Total IoT Cybersecurity Revenue from Other Security Solutions (m), Split by 8Key Regions, 2024-2029
- 7.2. Total Other Security Solutions Hardware Cost
- Figure and Table 7.2: Total Hardware Cost for Other Security Solutions per Annum (m), Split by 8Key Regions, 2024-2029








