 |
市場調查報告書
商品編碼
1641912
行動加密:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)Mobile Encryption - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
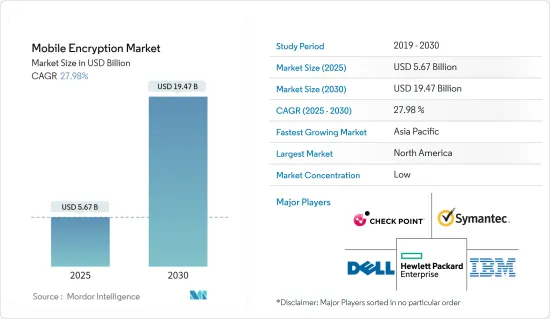
行動加密貨幣市場規模預計在 2025 年為 56.7 億美元,預計到 2030 年將達到 194.7 億美元,預測期內(2025-2030 年)的複合年成長率為 27.98%。
隨著企業適應日益普遍的監管和合規要求以及更嚴格的內部政策,主要企業採用加密的數量和範圍都在成長。
主要亮點
- 行動加密是使用某種語言或代碼對資料進行加密的過程,只有獲得授權的個人才能使用正確的解密金鑰來破解。由於人們對資料安全和隱私的擔憂日益加劇,市場正在迅速擴張。由於大多數人依賴行動裝置來儲存敏感資訊(如財務資料、個人資訊和機密商業機密),對行動加密解決方案的需求變得越來越重要。
- 高階威脅的出現和演變、雲端服務的日益普及、行動裝置的廣泛使用和虛擬是擾亂行動加密市場的關鍵因素。嚴格的合規和監管要求的需求以及對智慧財產權安全和隱私日益成長的擔憂是推動市場發展的主要因素。此外,各類終端用戶中「物聯網」的日益成長的趨勢也是推動行動加密市場擴張的關鍵因素。
- 行動加密可保護客戶資料不被外部人員獲取,確保其隱私和安全。隨著智慧型手機付款的使用增加,數位付款的數量急劇增加。為了改善現有的付款系統,公司正在將區塊鏈融入行動付款中。區塊鏈最大的特點就是有效性,為安全可靠的交易樹立了標竿。
- BYOD(自帶設備)現象及其在幾乎所有組織中的迅速普及,迫使人們從根本上重新思考安全方法,從而導致組織採用許多不同的加密技術。因此,有效、安全地管理策略和金鑰已成為日益艱鉅的挑戰。
- 隨著組織部署越來越多的行動勞動力,過去幾年對行動加密的需求急劇增加。行動勞動力有許多好處,包括提高生產力、降低開支和提高靈活性。隨著越來越多的企業繼續採用行動工作者,市場在過去幾年中實現了顯著成長,而且這一趨勢預計還將繼續下去。
- 不同行業對加密的綜合使用有很大差異。具體而言,採用率最高的是監管嚴格且依賴行動的行業,例如金融服務和 IT 服務,而採用率最低的是監管較少的行業,例如製造業和消費品。
- 此外,一個主要的障礙是組織沒有意識到行動加密解決方案的重要性。加密解決方案的複雜性、加密技術缺乏行業標準以及對加密可能對設備性能產生影響的擔憂是進一步的限制。
- 新冠疫情的封鎖和限制導致行動技術的使用比平常更高。隨著安全設備互通性需求的增加並成為新常態,對行動加密的需求預計將大幅增加。
行動加密貨幣市場趨勢
BFSI 預計將佔據主要市場佔有率
- 為了確保行動應用程式的安全,銀行採用了許多加密技術。對於傳輸中的資料,常見的技術有傳輸層安全性(TLS)和安全通訊端層(SSL),而對於靜止的資料,常見的技術有高級加密標準(AES)和RSA(RSA)。是一種技術。為了進一步保護客戶訊息,銀行還可以採用多因素身份驗證和設備指紋識別等額外的安全措施。推動這一成長的原因是銀行業對付款安全解決方案的需求不斷成長,以便為消費者提供更安全的服務。
- 目前已確定的將影響這一細分市場的趨勢之一是,使用加密的 OTP SMS 越來越受歡迎,可以避免網路釣魚、中間人攻擊和惡意軟體木馬等可能的攻擊。就是其中之一。由於客戶的大部分銀行帳戶資訊和密碼都儲存在他們的行動裝置上,甚至個人照片(在網路上申請貸款時)也是一個重大的安全隱患。 SSL/TLS 支援透過網路安全傳輸個人資料,例如信用卡資訊、密碼和其他敏感個人資訊。
- 銀行和金融機構使用 SSL/TLS 加密流量來解決其中的幾個問題,包括控制存取、保護機密性和減少針對特定通訊協定的攻擊。隨著線上交易變得越來越複雜,付款提供者正在努力跟上技術以提供更好的安全性。由於目前大多數線上付款都是行動支付或應用程式內付款,傳統的 PCI-DSS 標準需要進行適當升級。
- 此外,預計人工智慧(AI)的加入將提高金融加密軟體的效率和有效性。同時,它可以幫助組織和客戶滿足日益成長的資料保護需求。因此,我們可以預見銀行和金融領域將迅速採用基於人工智慧的加密軟體。
- 銀行必須在資料的整個生命週期中維護資料的完整性。因此,銀行必須制定適合其需求的適當的威脅偵測和回應程序。因此,銀行可以透過實施資料遮罩和加密軟體等各種安全標準來維護資料完整性。因此,銀行、金融和保險 (BFSI) 行業對金融加密軟體的需求預計將上升。
- 過時的 SSL 標準阻礙了 EMV 三域安全 (3DS) 等新舉措的使用。使用兩種平行演算法對通訊進行加密目前被認為是最強大的加密形式,密碼學家預測雙單元加密在整個預測期內仍將保持這種狀態。
預計北美將佔據較大的市場佔有率
- 在北美,美國企業越來越依賴電腦網路和電子資料來進行日常業務,個人和財務資訊透過行動電話傳輸並儲存在雲端的情況正在增加。此外,BYOD 趨勢的顯著上升也推動了對智慧卡、實體令牌和 KPI 等高級身份驗證方法的需求,以存取敏感資訊並登入用戶端伺服器。
- 這項優勢源自於加拿大和美國等國家不斷提高的監管標準,要求銀行加強資料隱私。為了保護隱私,公共銀行和私人銀行都對加密軟體的需求越來越大。此外,網路攻擊和對關鍵業務資訊的威脅的激增預計將刺激該地區的市場擴張。
- 在美國,估計約有 51% 的行動裝置具有全碟加密功能,預計未來幾年這一數字還會增加。然而,隨著全盤加密的廣泛採用,幾乎所有這些設備都有可能無法被執法部門存取。這就是政府監管加密貨幣市場的原因。谷歌等科技巨頭面臨限制和障礙。
- AAG IT Services 估計,到 2021 年,一半的美國網路用戶的帳戶將遭到入侵。十分之一的美國公司沒有針對網路攻擊的防禦措施。此外,2022 年上半年網路犯罪影響了 5,335 萬美國個人。因此,日益嚴格的個人資訊保護法和行動付款技術有望為該領域開闢新的產業前景。
- 蘋果是行動全盤加密領域的領導者,美國大約 55% 的行動裝置運行 iOS。北美的惡意資料外洩事件正在增加,並且是最大的加密服務市場。
行動加密行業概覽
全球行動加密貨幣市場是分散的,因為行動加密貨幣生態系統由各種行動加密貨幣解決方案和服務供應商組成。主要企業正在部署各種策略,如新產品發布、臨床試驗和市場計劃,透過大量投入研發、合資、夥伴關係和收購來擴大其在這個市場的影響力和創新。市場的主要企業包括 IBM 公司、HP Enterprises、戴爾、賽門鐵克和 Checkpoint Software。
- 2022 年 10 月 - 全球領先的網路安全解決方案供應商 Check Point Software Technologies Ltd. 獲得了以色列公司 Check Point 的認可,後者是開發人員的開發人員優先安全工具的領先創新者。新興企業Spectral。此次收購增強了 Check Point 的雲端解決方案 Check Point CloudGuard,使其具備了以開發人員為先的安全功能,從而提供最廣泛的雲端應用程式安全解決方案,包括基礎設施即程式碼(IaC) 掃描和硬編碼機密檢測。
- 2022 年 12 月 - RingCentral, Inc. 宣布正在擴展其旗艦產品 RingCentral MVP 的端對端加密 (E2EE) 功能,除了視訊之外,還包括電話通話和通訊。 E2EE技術保護使用者的通訊內容不被未授權存取。這不僅可以防止外部入侵和攻擊,還可以確保注重安全的組織的特權討論的隱私。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 調查結果
- 調查前提
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場動態
- 市場概況
- 市場促進因素與限制因素簡介
- 市場促進因素
- 企業對安全通訊的需求日益增加
- 資料安全和智慧財產權隱私問題日益令人擔憂
- 市場限制
- 缺乏意識和熟練勞動力
- 價值鏈/供應鏈分析
- 產業吸引力-波特五力分析
- 購買者/消費者的議價能力
- 供應商的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭對手之間的競爭強度
第5章 市場區隔
- 按組件
- 解決方案
- 服務
- 按應用
- 磁碟加密
- 文件/資料夾加密
- Web通訊加密
- 雲端加密
- 其他應用
- 依部署類型
- 本地
- 雲
- 按公司規模
- 中小企業
- 大型企業
- 按最終用戶
- BFSI
- 航太和國防
- 衛生保健
- 政府及公共機構
- 電訊
- 零售
- 其他最終用戶
- 按地區
- 北美洲
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東和非洲
第6章 競爭格局
- 公司簡介
- Dell
- Check Point Software Technologies, Ltd
- Hewlett Packard Enterprise
- IBM Corporation
- KoolSpan, Inc.
- MobileIron, Inc.
- SecurStar GmbH
- Silent Circle, LLC
- Sophos Ltd.
- Symantec Corporation
- T-Systems International GmbH
第7章投資分析
第8章 市場機會與未來趨勢
The Mobile Encryption Market size is estimated at USD 5.67 billion in 2025, and is expected to reach USD 19.47 billion by 2030, at a CAGR of 27.98% during the forecast period (2025-2030).

As organizations have adapted to increasingly pervasive regulatory and compliance mandates and more stringent internal policies, encryption deployments have increased in number and scope in significant enterprises.
Key Highlights
- Mobile encryption is the process of encoding data in a language or code only authorized individuals with the right decryption key can decipher. Due to increased worries about data security and privacy, the market is expanding quickly. The demand for mobile encryption solutions is becoming increasingly critical as most people utilize mobile devices to store sensitive information like financial data, personal information, and confidential corporate information.
- Increasing and evolving advanced threats, the enhanced adoption of cloud services, mobile device proliferation, and virtualization are the major factors creating disruptive changes in the mobile encryption market. The need for stringent compliance and regulatory requirements and increasing concern for the security and privacy of intellectual property are the major factors driving the market. Also, the rising trend of the Internet of Things among various end-user verticals is a crucial factor facilitating the expansion of the mobile encryption market.
- Mobile encryption safeguards customer data by making it unintelligible to outsiders, ensuring it remains private and secure. The number of digital payments has increased dramatically as a result of the rise in smartphone payment usage. To improve the present payment system, businesses are integrating blockchain with mobile payment. The most important feature of blockchain is its effectiveness, which establishes a benchmark for safe and secure transactions.
- The "bring your own device" (BYOD) phenomenon and its incredibly fast and pervasive adoption by almost every organization necessitated a fundamental rethinking of security approaches, and it has been found that organizations are deploying many disparate encryption platforms. As a result, managing policies and keys efficiently and securely is an increasingly troublesome challenge.
- The demand for mobile encryption has grown dramatically over the years as organizations increasingly deploy a mobile workforce. A mobile workforce has many advantages, including increased productivity, lower expenses, and more flexibility. As more businesses continue to employ a mobile workforce, the market has consequently experienced considerable expansion over the past few years, and this trend is projected to continue in the years to come.
- The comprehensive use of encryption varies considerably by industry segment. Specifically, heavily regulated and mobile-dependent industries, such as financial services and IT services, have the highest use rate, and less regulated industries, such as manufacturing and consumer products, have the lowest use rate.
- Additionally, one major barrier is that organizations do not recognize the importance of mobile encryption solutions. Concerns regarding the complexity of encryption solutions, the absence of industry standards for encryption technology, and the possible effects of encryption on device performance are some further limitations.
- COVID Lockdowns and limitations increased mobile technology use more than usual. As the need for security device interoperability grows and becomes the new standard, there will be a significant rise in demand for mobile encryption.
Mobile Encryption Market Trends
BFSI is Expected to Hold a Major Market Share
- For the security of their mobile apps, banks employ a number of encryption techniques. For data in transit, common techniques include Transport Layer Security (TLS) and Secure Sockets Layer (SSL), whereas for data at rest, common techniques include Advanced Encryption Standard (AES) or RSA. To further safeguard customer information, banks may additionally employ extra security measures like multi-factor authentication and device fingerprinting. The banking industry's expanding requirement for payment security solutions to offer its consumers a more secure service is what is causing the growth.
- Among the current identified trends influencing this segment of the market, the usage of encrypted OTP SMS is one of them, along with a PIN to avoid any possible attacks like phishing, man-in-the-middle attacks, and malware Trojans. As more of the bank account information and passwords of customers come on mobile devices, even personal pictures (while applying for loans online) have become a major security concern. SSL/TLS enables secure transmissions of private data over the internet, including credit card details, passwords, and sensitive personal information.
- Banks and financial institutions use SSL/TLS to encrypt their traffic to address these multiple issues, including controlling access, protecting confidentiality, and reducing exposure to protocol-specific attacks. With the increased sophistication of online transactions, payment providers are catching up with the technologies to provide better security. The majority of online payments are now mobile or in-app payments; the traditional PCI-DSS standards have to be suitably upgraded.
- Moreover, it is projected that the efficiency and effectiveness of financial encryption software would grow with the addition of artificial intelligence (AI). At the same time, it helps organisations and customers meet the growing demand for data protection. As a result, it is anticipated that encryption software powered by artificial intelligence would be quickly adopted by the banking and finance sector.
- The integrity of the data must be maintained by the banks throughout the life of the data. As a result, it is essential for banks to put in place the appropriate threat detection and response procedures in accordance with their needs. Thus, by imposing various security standards, such as data masking and encryption software by banks, the data integrity can be preserved. As a result, it is anticipated that the banking, finance, and insurance (BFSI) industry will see an increase in demand for financial encryption software.
- The outdated SSL standards prevent the use of new initiatives like EMV Three-Domain Secure (3DS), a messaging mechanism that enables customers to authenticate themselves with their card issuer when making card-not-present online purchases.. Communication that uses two algorithms for encryption that work side-by-side is currently considered the strongest encryption, with cryptologists predicting double-cell encryption to remain so over the forecast period.
North America is Expected to Hold a Major Market Share
- In the North American region, the United States business sector increasingly depends on computer networks and electronic data to conduct its daily operations, and growing pools of personal and financial information are also transferred and stored in the cloud using phones. Furthermore, a significant increase in the BYOD trend is also favoring the conditions for advanced authentication methods, such as smart cards, physical tokens, and KPIs, to access sensitive information or log in to client servers.
- The dominance can be attributed to the more stringent regulatory standards in nations like Canada and the United States, which oblige banks to increase data privacy. In order to protect privacy, both public and private banks have increased their demand for cryptographic software. Additionally, the regional market expansion is anticipated to be fueled by the surge in cyberattacks and the threat to business-critical information.
- It is estimated that around 51% of mobile devices in the United States have full disk encryption, which is expected to increase in the coming years. However, with the growth in the adoption of full disk encryption, almost all these devices could become inaccessible to law enforcement. As a result, the government is regulating the encryption market. Companies like Google and other tech giants are facing restrictions and obstacles.
- AAG IT Services estimates that in 2021, 1 in 2 American internet users had their accounts breached. One in ten US businesses do not have any protection against cyberattacks. In addition, cybercrime had an impact on 53.35 million US individuals in the first half of 2022. Therefore, rising privacy laws and mobile payment technology are anticipated to open up new industry prospects in the area.
- Apple is the largest provider of mobile full-disk encryption, and around 55% of the mobile devices in the United States run on iOS. With increased malicious data breaches occurring in the North American region, it has become the largest market for encryption services.
Mobile Encryption Industry Overview
The Global Mobile Encryption Market is fragmented, as the mobile encryption ecosystem comprises various mobile encryption solutions and service providers. The major players deploy various strategies, such as new product launches and clinical trials, and are also taking market initiatives and innovations through high expenditure on research and development, joint ventures, partnerships, acquisitions, and others to increase their footprints in this market. Some of the major players in the market are IBM Corporation, HP Enterprises, Dell, Symantec, and Checkpoint Software, among others.
- October 2022 - Check Point Software Technologies Ltd., a top global provider of cyber security solutions, acquired Spectral, an Israeli startup that was a key innovator in developer-first security tools created by developers for developers. With this purchase, Check Point was expected to increase the developer-first security capabilities of its cloud solution, Check Point CloudGuard, and offer the broadest range of cloud application security use cases, including infrastructure as code (IaC) scanning and hardcoded secret detection.
- December 2022 - RingCentral, Inc. announced that it is extending End-to-End Encryption (E2EE) capabilities in its flagship RingCentral MVP product to encompass both phone and messaging in addition to video. E2EE technology shields users' communication content from being accessed by unauthorised parties. This offers protection against infiltration and attacks from outside parties as well as privacy for privileged discussions for security-conscious organisations.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Study Assumptions
- 1.3 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Growing demand for secure communication in enterprises
- 4.3.2 Increasing concern for data security and privacy of intellectual property
- 4.4 Market Restraints
- 4.4.1 Lack of awareness and skilled workforce
- 4.5 Value Chain / Supply Chain Analysis
- 4.6 Industry Attractiveness - Porter's Five Forces Analysis
- 4.6.1 Bargaining Power of Buyers/Consumers
- 4.6.2 Bargaining Power of Suppliers
- 4.6.3 Threat of New Entrants
- 4.6.4 Threat of Substitute Products
- 4.6.5 Intensity of Competitive Rivalry
5 MARKET SEGMENTATION
- 5.1 Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 Application
- 5.2.1 Disk Encryption
- 5.2.2 File/Folder Encryption
- 5.2.3 Web Communication Encryption
- 5.2.4 Cloud Encryption
- 5.2.5 Other Applications
- 5.3 Deployment Type
- 5.3.1 On-premise
- 5.3.2 Cloud
- 5.4 Enterprise Size
- 5.4.1 SMEs
- 5.4.2 Large Enterprises
- 5.5 End Users
- 5.5.1 BFSI
- 5.5.2 Aerospace and Defense
- 5.5.3 Healthcare
- 5.5.4 Government and Public Sector
- 5.5.5 Telecom
- 5.5.6 Retail
- 5.5.7 Other End Users
- 5.6 Geography
- 5.6.1 North America
- 5.6.2 Europe
- 5.6.3 Asia Pacific
- 5.6.4 Latin America
- 5.6.5 Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Dell
- 6.1.2 Check Point Software Technologies, Ltd
- 6.1.3 Hewlett Packard Enterprise
- 6.1.4 IBM Corporation
- 6.1.5 KoolSpan, Inc.
- 6.1.6 MobileIron, Inc.
- 6.1.7 SecurStar GmbH
- 6.1.8 Silent Circle, LLC
- 6.1.9 Sophos Ltd.
- 6.1.10 Symantec Corporation
- 6.1.11 T-Systems International GmbH




