 |
市場調查報告書
商品編碼
1642005
威脅情報:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)Threat Intelligence - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
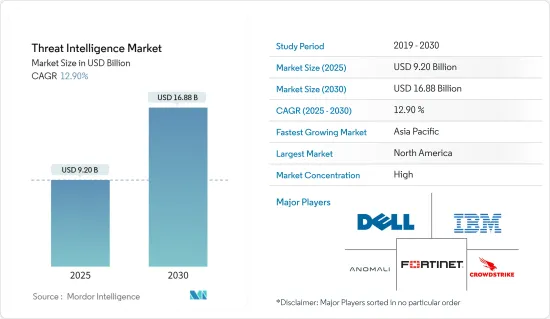
威脅情報市場在 2025 年的價值預估為 92 億美元,預計到 2030 年將達到 168.8 億美元,在市場估計和預測期(2025-2030 年)內以 12.9% 的複合年成長率成長。
在過去的幾年中,攻擊源、目標、攻擊概況和不同類型的技術之間發生了模式轉移。攻擊的來源仍然是一個問題,因為雖然可以識別攻擊的類型和目標,但很難確定誰實施了攻擊。
主要亮點
- 隨著攻擊和資料外洩的增加,企業將重點轉向各種網路安全解決方案。隨著攻擊者和防禦者之間的網路軍備競賽愈演愈烈,越來越多的組織開始轉向網路情報。威脅情報使防禦者能夠採取更快、更明智的安全行動,以便在發生攻擊時從被動行為轉變為主動行為。
- 大多數組織將情報工作重點放在基於現有案例研究和攻擊的更基本的使用案例上,例如將情報來源整合到現有的IPS、防火牆和SIEM 中,而情報資訊對結果影響不大。並未充分體現利用了。
- 威脅情報市場的主要驅動力是攻擊技術日益獨特以及資料的弱化。推動這一市場的主要因素是各類企業產生的資料量不斷增加。
- 透過整合雲端和威脅情報,公司可以利用全球威脅社群主動偵測未知威脅,並透過縮小關注範圍來防止攻擊變得明顯,從而保護自己免受網路威脅。這導致威脅情報解決方案的採用顯著增加。
- 近年來,網路犯罪數量不斷增加,且沒有減緩的跡象。由於疫情的影響,在家工作增加。網路攻擊的數量正在增加。隨著企業採用遠距工作模式,威脅情報市場對企業安全的擔憂日益加劇。
- COVID-19 疫情對市場發展產生了積極影響,世界各國政府正在製定新策略來支持組織對網路安全的擔憂。日益增多的網路漏洞正在推動威脅情報市場的成長。
威脅情報市場趨勢
BFSI 部門預計將佔據主要佔有率
- BFSI 產業是關鍵基礎設施產業之一,由於其基本客群規模和金融資訊的敏感性,該產業持續面臨大量資料外洩和網路攻擊。
- 網路犯罪分子正在最佳化一系列災難性的網路攻擊,以破壞金融部門。這是因為網路攻擊是一種利潤豐厚的經營模式,可以產生巨額回報,同時還具有風險相對較低、易於偵測的優勢。這些攻擊的威脅包括 ATM 惡意軟體、木馬、惡意軟體、勒索軟體、行動銀行惡意軟體、資料外洩、組織入侵、資料竊取和逃稅。
- 作為保護 IT 流程和系統的策略的一部分,公共和私人銀行都專注於採用未授權存取技術來防止網路攻擊,同時遵守政府法規並保護敏感的客戶資料。此外,不斷成長的客戶期望、技術進步和監管要求迫使銀行機構採取積極主動的安全措施。
- 隨著網路銀行、行動電話銀行等科技和數位管道的日益普及,網路銀行正成為客戶使用銀行服務的首選。銀行必須使用高階身份驗證和存取控制流程,例如威脅情報策略。
北美佔有最大市場佔有率
- 美國金融服務業儲存的資料超過Exabyte 。這些資料來自各種來源,包括信用卡和簽帳金融卡歷史記錄、客戶銀行存取歷史記錄、銀行交易量、通話記錄、帳戶交易和網路互動。
- 有了合適的基礎設施,許多全球金融機構正在增加對物聯網設備的使用,北美威脅情報解決方案的成長將由網路使用者推動。
- 該地區的公共和私營部門組織正在投資研發先進的威脅情報解決方案。美國國防安全保障部(DHS)網路安全和基礎設施安全局(CISA)報告稱,其正在監控使用COVID-19 主題誘餌的網路釣魚和惡意軟體傳播,以及包含冠狀病毒和COVID-19 相關語言的新型惡意軟體。
- 投資威脅情報解決方案對於加強一個國家的安全態勢至關重要。為了確保整個北美的無縫和安全營運,各組織將受益於威脅情報解決方案的實施。
威脅情報業概況
威脅情報市場正在整合並由少數幾家大公司主導,導致更多安全的軟體解決方案被推出。 Dell Inc.、IBM Corporation、Anomali Inc.、Fortinet Inc. 和 CrowdStrike Inc. 是市場上提供專用威脅情報解決方案的主要企業。
- 2023 年 12 月-Fortinet 宣布發布最新版整合操作技術(OT) 安全解決方案與服務。這些新增功能使 Fortinet 的 OT 安全平台與市場其他產品的差距進一步拉大。
- 2023 年10 月- IBM 公司宣布其託管檢測和響應服務將採用新的AI 技術進行下一次演進,包括能夠自動升級或關閉高達85% 的警報,1 有助於縮短客戶的安全響應時間。助於縮短生產線。全新威脅偵測和回應服務 (TDR) 可全天候查看客戶混合雲端環境中所有相關技術的安全警報,包括現有安全工具和投資以及雲端、本地和營運技術 (OT)。補救。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 研究假設和市場定義
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場洞察
- 市場概況
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 購買者/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭強度
- 產業價值鏈分析
- COVID-19 市場影響評估
第5章 市場動態
- 市場促進因素
- 安全漏洞和網路犯罪不斷增加
- 下一代安全解決方案的演變
- 市場挑戰/限制
- 資料安全預算低,解決方案實施成本高
第6章 市場細分
- 按類型
- 解決方案
- 按服務
- 按部署
- 本地
- 雲
- 按最終用戶產業
- BFSI
- 資訊科技/通訊
- 零售
- 製造業
- 衛生保健
- 其他最終用戶產業
- 按地區
- 北美洲
- 美國
- 加拿大
- 歐洲
- 英國
- 德國
- 法國
- 其他歐洲國家
- 亞太地區
- 中國
- 日本
- 印度
- 澳洲
- 其他亞太地區
- 拉丁美洲
- 墨西哥
- 巴西
- 其他拉丁美洲國家
- 中東和非洲
- 阿拉伯聯合大公國
- 南非
- 其他中東和非洲地區
- 北美洲
第7章 競爭格局
- 公司簡介
- Juniper Networks Inc.
- AlienVault Inc.
- Farsight Security Inc.
- Trend Micro Incorporated
- LogRhythm Inc.
- F-Secure Corporation
- Check Point Software Technologies Ltd
- Dell Inc.
- IBM Corporation
- Webroot Inc.
- Fortinet Inc.
- Broadcom Inc.(Symantec Corporation)
- McAfee LLC
- LookingGlass Cyber Solutions Inc.
- FireEye Inc.
第8章投資分析
第9章:市場的未來
The Threat Intelligence Market size is estimated at USD 9.20 billion in 2025, and is expected to reach USD 16.88 billion by 2030, at a CAGR of 12.9% during the forecast period (2025-2030).

A paradigm shift has taken place in the last few years between attack sources, targets, destination attacks profiles and different types of technology. While it is possible to identify attack types and targets, the source of those attacks remains a problem due to difficulties in determining who was responsible for them.
Key Highlights
- Organizations are shifting their focus to different cyber security solutions in view of the increasing number of attacks and data breaches. Due to the increasing cyber arms race among attackers and defenders, a growing number of organisations are focusing their attention on cyber intelligence. Thanks to threat intelligence, defenders have been able to make quicker and more informed security decisions with a view to moving their behaviour from reactive to proactive in the event of an attack.
- Most organizations focus their intelligence efforts on more basic use cases, which are based on existing case studies and attacks, such as integrating intelligence feeds with existing IPS, firewalls and SIEMs, and do not take full advantage of the intelligence information they have to offer.
- The market for threat intelligence is primarily driven by the increasing uniqueness of the attack techniques, which makes the data vulnerable. The key factor driving this market is the increasing volumes of data generated by different enterprises.
- By integrating cloud and threat intelligence, organisations can protect themselves against cyber threats by using the Global Threat Community to detect unknown threats before they become known in order to prevent them from emerging so as to target an attack's surface. This has led to a significant increase in the adoption of threat intelligence solutions.
- The number of cyber crimes has increased in recent years, but there is no sign they are slowing down. telecommuting has increased as a result of the pandemic. The number of cyberattacks is increasing. The market for threat intelligence is further driven by the adoption of a remote working model by enterprises, which raises concerns about corporate security.
- The COVID 19 pandemic has had a positive impact on market growth, and new strategies are being developed by governments around the world to support organisations' concerns about cyber security. An increase in cyber vulnerabilities is driving the growth of threat intelligence markets.
Threat Intelligence Market Trends
BFSI Segment is Expected to Occupy a Significant Share
- Due to its large customer base, which the BFSI sector serves and due to the Financial Information at stake, it is one of the critical infrastructure segments facing a number of data breaches and cyber attacks on an ongoing basis.
- Cyber criminals optimize many calamitous cyberattacks to immobilize the financial sector because they are a highly lucrative business model with spectacular returns and an added upside of relatively low risk and detection. The threat landscape of these attacks ranges from ATM malware, Trojans, malware, ransomware, and mobile banking malware to data breaches, institutional intrusions, data thefts, tax evasion, etc.
- Public and privately owned banks are focusing on the implementation of new technology to prevent cyber attacks, as part of a strategy for safeguarding IT processes and systems, ensuring critical customer data is protected against unauthorised access while respecting government rules. Moreover, a proactive approach to security is required by banking institutions in view of increasing customer expectations, technical advances and legislative requirements.
- Online banking is becoming a favourite choice for customers of banking services due to the growing penetration of technology and digital channels, e.g. internet banking and cellphone banking. Advanced authentication and access control processes, such as threat intelligence strategies, must be used by the banks.
North America to Hold the Largest Market Share
- There are more than 1 exabyte of stored data in the financial services industry in the United States. These data are collected from different sources, such as credit and debit card history, customer bank visits, banking volumes, call logs, account transactions or web interactions.
- A number of global financial institutions have increased their use of Internet of Things devices due to the availability of adequate infrastructure, and the growth of threat intelligence solutions in North America is expected to be driven by Internet users.
- In order to develop advanced threat intelligence solutions, public authorities and private players in different regions are investing in research and development. The US Department of Homeland Security (DHS) Cybersecurity and the Infrastructure Security Agency (CISA) mentioned that they experienced a massive rise in phishing and malware distribution using COVID-19-themed lures, registration of new domain names containing wording related to coronavirus or COVID-19, and attacks against newly and rapidly deployed remote access and teleworking infrastructure.
- In order to strengthen the security posture of a country, investments in threat intelligence solutions are essential. In order to ensure a seamless and secure operation throughout North America, organizations will benefit from the deployment of threat intelligence solutions.
Threat Intelligence Industry Overview
The threat intelligence market is consolidated and dominated by a few major players, with more secure software solutions being launched. Dell Inc., IBM Corporation, Anomali Inc., Fortinet Inc., and CrowdStrike Inc. are key players in the market that offer dedicated solutions for threat intelligence.
- December 2023 - Fortinet, Inc has announced the latest release of new, integrated operational technology (OT) security solutions and services. These additions further distance Fortinet's OT Security Platform from the rest of the market.
- October 2023 - IBM Corporation has launched the next evolution of its managed detection and response service offerings with new AI technologies, including the ability to automatically escalate or close up to 85% of alerts,1 helping to accelerate security response timelines for clients., Wher the new Threat Detection and Response Services (TDR) provide 24x7 monitoring, investigation, and automated remediation of security alerts from all relevant technologies across client's hybrid cloud environments - including existing security tools and investments, as well as cloud, on-premise, and operational technologies (OT).
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Industry Value Chain Analysis
- 4.4 Assessment of Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Growing Incidences of Security Breaches and Cyber Crime
- 5.1.2 Evolution of Next-generation Security Solutions
- 5.2 Market Challenges/restraints
- 5.2.1 Low Data Security Budget and High Installation Cost of Solution
6 MARKET SEGMENTATION
- 6.1 By Type
- 6.1.1 Solutions
- 6.1.2 Services
- 6.2 By Deployment
- 6.2.1 On-premise
- 6.2.2 Cloud
- 6.3 By End-user Industry
- 6.3.1 BFSI
- 6.3.2 IT and Telecommunications
- 6.3.3 Retail
- 6.3.4 Manufacturing
- 6.3.5 Healthcare
- 6.3.6 Other End-user Industries
- 6.4 By Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 United Kingdom
- 6.4.2.2 Germany
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia-Pacific
- 6.4.3.1 China
- 6.4.3.2 Japan
- 6.4.3.3 India
- 6.4.3.4 Australia
- 6.4.3.5 Rest of Asia-Pacific
- 6.4.4 Latin America
- 6.4.4.1 Mexico
- 6.4.4.2 Brazil
- 6.4.4.3 Rest of Latin America
- 6.4.5 Middle East and Africa
- 6.4.5.1 United Arab Emirates
- 6.4.5.2 South Africa
- 6.4.5.3 Rest of Middle East and Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Juniper Networks Inc.
- 7.1.2 AlienVault Inc.
- 7.1.3 Farsight Security Inc.
- 7.1.4 Trend Micro Incorporated
- 7.1.5 LogRhythm Inc.
- 7.1.6 F-Secure Corporation
- 7.1.7 Check Point Software Technologies Ltd
- 7.1.8 Dell Inc.
- 7.1.9 IBM Corporation
- 7.1.10 Webroot Inc.
- 7.1.11 Fortinet Inc.
- 7.1.12 Broadcom Inc. (Symantec Corporation)
- 7.1.13 McAfee LLC
- 7.1.14 LookingGlass Cyber Solutions Inc.
- 7.1.15 FireEye Inc.












