 |
市場調查報告書
商品編碼
1630351
嵌入式安全 -市場佔有率分析、產業趨勢/統計、成長預測(2025-2030)Embedded Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
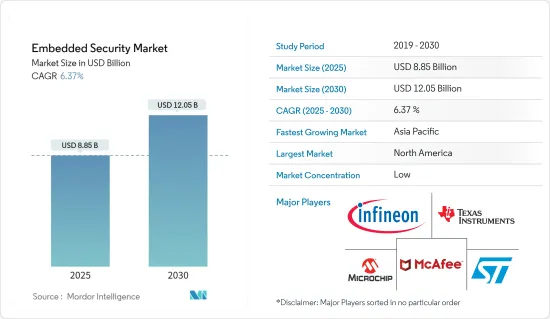
嵌入式安全市場規模預計到 2025 年為 88.5 億美元,預計到 2030 年將達到 120.5 億美元,在市場估計和預測期間(2025-2030 年)複合年成長率為 6.37%。
穿戴式裝置、智慧型手機和平板電腦、汽車、智慧ID卡、工業、付款處理和卡片以及電腦等各種應用程式對嵌入式安全解決方案的需求不斷成長,正在推動該市場的成長。此外,BYOD(自帶設備)趨勢的激增正在推動全球對嵌入式安全解決方案的需求。
主要亮點
- 內建安全性旨在保護處理資料和持卡人資料。內建安全性降低了可能導致財務和聲譽損失的資料外洩風險。它還有助於滿足 PCI DSS(支付卡產業資料安全標準)標準。安全元件、可信任執行環境 (TEE) 和防篡改硬體是付款處理和卡片中使用的內建安全性的範例。這些內建安全解決方案專門防止持卡人資料被攻擊者破壞。
- 科技的進步比以往任何時候都快。科技每天都在進步,引入新的方法和功能。這不僅僅是電腦和行動應用程式。其中包括人工智慧和基於物聯網的小工具,它們在人類日常生活中廣泛採用。物聯網的興起正在蔓延到所有產業,其應用範圍包括工業自動化、醫療設備、航空、穿戴式科技、智慧家居和汽車。隨著物聯網應用的擴大,連網設備中各種安全漏洞的可能性也增加。它還增加了外部網路威脅攻擊運作中的系統並導致設備故障或損壞的可能性。此外,內建安全裝置也不斷增加,以避免此類情況的發生。
- 電動車市場正在不斷發展和成熟。客戶正在積極尋找不使用傳統石化燃料的車輛。這些車輛必須具有成本效益並且對環境有益。此外,為了滿足這些需求,需要在家庭和道路上安裝充電站。充電站的安全對於保護其關鍵基礎設施至關重要。電動車和充電站具有複雜的設計和多重安全問題,因此很難管理系統內的所有安全挑戰。內建設備安全系統可以幫助解決這個問題。由於嵌入和連接到車輛的軟體數量不斷增加,電動車的安全性至關重要。
- 這些系統近年來越來越受歡迎。然而,實體安全設備加上通訊安全設備的基本成本高於傳統安全系統的成本。安防系統中使用的發射器、接收器和感測器等內部組件價格較高,直接影響系統的主要售價。此外,更新現有安全系統和採用新的整合技術對於小型企業和個人用戶來說成本高昂。
- 然而,無論軟體本身多麼複雜或具有安全意識,都無法保證嵌入式系統的安全。雲端、軟體和硬體供應商必須共同努力。例如,片上安全功能可實現強大的金鑰管理和加密,這對於單獨的內建軟體來說運算量要求過高,而硬體技術可確保裝置啟動完整性。路徑空間控制、無根執行、加密檔案系統、存取控制規則和威脅等級異常偵測等功能由硬體功能啟用並安裝在作業系統中。
- 此外,萬事達卡新支付指數顯示,94% 的沙烏地阿拉伯消費者正在考慮在 2022 年使用至少一種新付款方式,包括加密貨幣、生物識別、非接觸式和2D碼。此外,68% 的受訪者表示正在嘗試一種他們通常不會嘗試的新支付方式。 COVID-19 大流行促使公民嘗試其他付款方式,並獲得速度和便利性的好處。預計此類發展將對市場發展產生正面影響。
嵌入式安全市場趨勢
穿戴式裝置在醫療領域的普及可望推動市場
- 根據蓋洛普年度健康與醫療調查,90% 的美國消費者表示他們目前使用穿戴式健身追蹤器,同樣比例的消費者目前使用行動醫療應用程式。此外,隨著美國國民醫療保健支出的增加,目前的使用情況以及表示過去使用過此類設備的美國公民的比例已增加至三分之一的美國公民,他們透露曾經使用過此類設備。環或智慧型手錶等健身追蹤器 (34%) 或透過行動電話或平板電腦上的應用程式追蹤健康統計資料 (32%)。
- 大多數穿戴式裝置使用各種感測器和其他技術來直接從佩戴者的身體和周圍環境收集和過濾資料。一些穿戴式裝置能夠在本地處理和分析資料,使用戶能夠即時存取結果和警報。此外,有些感測器和儲存設備太小,無法在源頭處理資料。相反,它透過藍牙或 Wi-Fi 將訊息發送到您的智慧型手機、雲端應用程式或遠端電腦。
- 在對資料進行分析和分析後,佩戴者透過智慧型手機應用程式或穿戴式裝置本身獲得可操作的見解。專有伺服器通常位於資料中心或雲端中,用於無限期地儲存原始資料和分析結果。通訊網路對於穿戴式技術的成功至關重要,因為它們能夠促進感測器和控制系統之間的通訊。透過減少端對端延遲,5G 技術的出現使這些網路速度更快,更有能力支援先進的穿戴式裝置。
- 根據《自然醫學》雜誌上發表的一項研究,穿戴式健身健身旨在透過創建一個可檢測 80% 的症狀前和無症狀感染的系統來檢測 COVID-19。這項研究涉及 3,300 多名年齡在 18 歲到 80 歲之間的成年人,他們的 Android 或 Apple 裝置上安裝了研究人員的應用程式 MyPHD。該應用程式從他們已有的穿戴式設備中收集資料,並將其傳輸到安全的雲端伺服器,研究人員可以在其中分析資料。穿戴式裝置包括 Fitbit、Apple Watch、Garmin 裝置以及與 Apple HealthKit 或 Google Fit 平台相容的其他小工具。
- 此外,科技服務公司 Vee Technologies 和教育機構 Sona Group 最近與多倫多大學健康網路 (UHN) 簽署了一項協議,開發基於智慧織物的穿戴式設備。該舉措將有助於開發智慧紡織品和服裝,以滿足加拿大醫療保健行業不斷成長的需求。這項合作研究協議旨在為 FIBRE 做出貢獻,FIBRE 是公立研究和教學醫院大學健康網路 (UHN) 的研究計劃。
北美佔據主要市場佔有率
- 北美在嵌入式安全市場佔有主要佔有率。這是由於人們越來越擔心關鍵基礎設施和敏感資料的保護,導致近年來地方政府機構加強了干涉。因此,特定預算分配和強制性安全措施等政府措施預計將推動北美嵌入式安全市場的發展。
- 物聯網設備的激增有望使基礎設施更有效率、更易於監控並提高生活品質,但也帶來了新的安全威脅。在物聯網環境中,所有智慧型裝置都連接到網際網路,它們產生和使用的資料儲存在容易受到駭客攻擊的伺服器上。這些因素產生了對內建安全性的需求。
- 整合到安全嵌入式硬體中的感測器的使用取決於特定公司所處的行業。例如,如果最終用戶正在種植農作物,則可以使用無人機檢查大片土地。物聯網設備可協助定位卡車車隊中的每批貨物,並預測到達目的地所需的時間。如果最終用戶經營製造工廠,他們可以使用連結的物聯網感測器來確定特定設備是否需要維修或使用嵌入式安全解決方案來提高組裝效率。
- 為了保護我們的系統免受入侵,經銷商和 Cars.com 實施了兩步驟登入流程。據 Helion Technologies 稱,多家保險公司都要求將其作為其經銷商網路安全保險的要求。此外,五年內保護加拿大基礎設施的新預算支出定為 1.449 億加元,其中包括加拿大金融、通訊、能源和運輸行業的關鍵網路系統,以及嵌入式安全解決方案,進一步刺激了需求。
- 美國聯邦法律《健康保險互通性與課責法案》顯示,資料外洩事件每年資料25%,據報告總合有 29,298,012 份醫療記錄遭洩露。預計這種成長將推動所研究的市場。
嵌入式安全產業概述
嵌入式安全市場高度細分,主要企業正在使用各種策略來擴大其在該市場的影響力,包括新產品發布、擴張、協議、合作夥伴關係和收購。此類新興市場的發展導致了市場競爭的激烈。主要企業包括英飛凌科技股份公司和意法半導體。
2024 年 3 月,商業嵌入式 Linux 解決方案供應商 Monta Vista Software LLC 宣布發布 CG X 5.0。電信級 Linux 產品線的第 15 個重要迭代透過引入許多先進的安全改進和更新,凸顯了 Monta Vista 對安全、可靠和創造性嵌入式系統開發的奉獻精神。
2024 年 2 月,嵌入式系統和技術發明的產業領導者 LDRA 宣布,嵌入式安全高峰會(ESSS) 將於 2024 年 7 月在印度各地舉行。
其他好處
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章簡介
- 研究成果
- 研究場所
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場動態
- 市場概況
- 市場促進因素
- 由於物聯網應用的增加,對物聯網安全的需求不斷成長
- 穿戴式裝置在醫學領域的應用
- 市場限制因素
- 由於 COVID-19 的影響,需求減少
- 由於缺乏審核而不遵守政府法規
- 產業價值鏈分析
- 產業吸引力-五力分析
- 新進入者的威脅
- 買家/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭公司之間敵對關係的強度
第5章市場區隔
- 元件類型
- 硬體
- 軟體
- 服務
- 應用
- 付款
- 認證
- 內容保護
- 其他
- 最終用戶
- 車
- 醫療保健
- 消費性電子產品
- 通訊設備
- 航太/國防
- 其他
- 地區
- 北美洲
- 美國
- 加拿大
- 歐洲
- 德國
- 英國
- 法國
- 歐洲其他地區
- 亞太地區
- 印度
- 中國
- 日本
- 其他亞太地區
- 其他
- 拉丁美洲
- 中東/非洲
- 北美洲
第6章 競爭狀況
- 公司簡介
- Infineon Technologies AG
- STMicroelectronics NV
- Texas Instruments Inc.
- McAfee LLC
- Microchip Technology Inc.
- Intellias Ltd
- Karamba Security Ltd
- Samsung Electronics Co.
- Idemia Group
- Rambus Incorporated
第7章 投資分析
第8章 市場機會及未來趨勢
The Embedded Security Market size is estimated at USD 8.85 billion in 2025, and is expected to reach USD 12.05 billion by 2030, at a CAGR of 6.37% during the forecast period (2025-2030).

The increasing need for embedded security solutions in various applications, such as wearables, smartphones and tablets, automotive, smart identity cards, industrial, payment processing and cards, and computers, is driving the growth of this market. Furthermore, the burgeoning Bring Your Own Device (BYOD) trend is boosting global demand for embedded security solutions.
Key Highlights
- Embedded security is implemented to safeguard the processing and cardholder data. The usage of embedded security serves to reduce the danger of data breaches, which can result in financial losses and reputational damage. It also aids in meeting the criteria of the Payment Card Industry Data Security Standard (PCI DSS). Secure elements, Trusted Execution Environment (TEE), and tamper-resistant hardware are examples of embedded security used in payment processing and cards. These embedded security solutions prevent cardholder data from being compromised by attackers, among other things.
- Technology is advancing faster than ever before. Every day, technology advances and introduces new approaches and functions. It is not just about computers and mobile applications. It is all about artificial intelligence and IoT-based gadgets, widely employed in everyday human life. The rise of IoT is spreading across all industries as it is utilized in various applications, including industrial automation, healthcare equipment, aviation, wearable technologies, smart home units, and automobiles. The growing use of IoT raises the possibility of different security vulnerabilities with connected devices. This also raises the likelihood of external cyber threats attacking running systems, causing the device to malfunction and cause harm. Also, embedded security devices are on the rise to avoid this condition.
- The market for electric vehicles is constantly evolving and maturing. Customers are aggressively seeking vehicles that do not use traditional fossil fuels. These vehicles should be both cost-effective and environmentally beneficial. Also, to meet these needs, an increasing number of electric charging stations must be established in homes and roadways. The security of charging stations is vital to protect its critical infrastructure. The complicated design and multiple safety concerns in electric vehicles and charging points make managing all security challenges in the system tough. Embedded device security systems help with this problem. Electric vehicle security is critical due to the rising number of embedded and connected software in cars.
- These systems have gained popularity in recent years. However, the basic cost of a single physical security device plus a communication security device is more than the cost of a traditional security system. Internal components like transmitters, receivers, and sensors utilized in security systems are more expensive, directly impacting the system's primary selling price. Furthermore, renewing existing security systems and adopting new integrated technology is not cost-viable for SME enterprises and individual users.
- However, the software itself cannot ensure the security of embedded systems, no matter how sophisticated and security aware. Cloud, software, and hardware vendors must collaborate. For instance, on-chip security features allow robust key management and encryption, which is too computationally demanding for embedded software alone, and hardware technologies secure device boot integrity. Functions like path space control, rootless execution, encrypted file systems, access control rules, and threat-level anomaly detection are made feasible by hardware capabilities and installed in the operating system.
- Furthermore, the Mastercard New Payments Index reported that 94% of Saudi Arabian consumers considered using at least one emerging payment method, such as cryptocurrency, biometrics, contactless, or QR code, in 2022. Furthermore, 68% of respondents reported trying a new payment method, which they would not have under normal circumstances. The COVID-19 pandemic pushed the country's population to try alternative payment methods and reap the benefits of timeliness and convenience. Such developments are expected to impact the market studied positively.
Embedded Security Market Trends
Increasing Adoption of Wearable Devices in Healthcare Expected to Drive the Market
- According to Gallup's annual Health and Healthcare survey, 90% of US consumers said they are currently using a wearable fitness tracker, and the same percentage stated that they currently use a mobile health application. Also, with the rise in national health expenditure in the United States, by combining the present use with the percentages of US citizens that claim, in the past, they have used such devices, it becomes clear that at some point, one in three citizens used a fitness tracker such as a wristband or smartwatch (34%) or tracked their health statistics on the phone or tablet application (32%).
- The majority of wearables collect and filter data directly from the wearer's body or from the environment around them using a range of sensors and other technologies. Certain wearables have the ability to process and analyze data locally, giving users instant access to results or alarms. Others are unable to process data at the source due to the small size of the sensors and storage devices. Rather, they will send the information to a smartphone, cloud app, or distant computer over Bluetooth or Wi-Fi.
- Following the analysis and parsing of data, the wearer will receive actionable insights via their smartphone application or the wearable device itself. Usually, proprietary servers in a data center or cloud will be used to keep original data and analytic results indefinitely. Due to their ability to facilitate communication between sensors and control systems, communication networks are essential to the success of wearable technology. With decreased end-to-end latency, these networks are growing quicker and more capable of supporting sophisticated wearables with the advent of 5G technology.
- According to a study published in Nature Medicine, wearable fitness trackers were designed to detect COVID-19 by building a system that detected 80% of pre-symptomatic and asymptomatic infections. The study involved more than 3,300 adults aged 18-80 who installed the researchers' app, called MyPHD, on their Android or Apple devices. The app collected data from the wearables they already had and transferred it to a secure cloud server where the researchers could analyze the data. The wearables included Fitbits, Apple Watches, Garmin devices, and other gadgets compatible with either Apple's HealthKit or the Google Fit platforms.
- Further, technology services firm Vee Technologies and Sona Group of educational institutions recently signed an agreement with Toronto-based University Health Network (UHN) to develop smart fabric-based wearables. This initiative will help develop smart textiles and garments that can support the growing needs of the healthcare industry in Canada. The collaboration agreement seeks to contribute to FIBRE, a research initiative by The University Health Network (UHN), a public research and teaching hospital.
North America Accounts for a Significant Market Share
- North America accounts for a significant share of the embedded security market, as growing concerns for protecting critical infrastructure and sensitive data have increased interventions by regional government bodies in recent years. Thus, government initiatives, such as specific budget allocations and mandated security policies, are expected to drive the market of embedded security in North America.
- The proliferation of IoT devices promises to improve infrastructure efficiency, ease of monitoring, and quality of life, but it also poses new security threats. In the IoT landscape, all smart gadgets are by nature Internet-connected, with the data they generate and utilize kept on servers that are vulnerable to hacking. These factors make embedded security necessary.
- The use of sensors integrated into security-embedded hardware can vary based on the industry in which a specific company operates. For instance, drones can be used to inspect big expanses of land if end users are cultivating crops. IoT devices can assist in locating each shipment in a fleet of trucks and in estimating the time it will take to reach its destination. If end users run a manufacturing plant, they can use linked IoT sensors to determine whether a specific piece of equipment needs repair or to find out how efficient the assembly line is with the help of embedded security solutions.
- To protect their system from intrusions, dealerships and Cars.com implemented a two-step login process. According to Helion Technologies, several insurers need it as a requirement for dealership cybersecurity coverage. Further, the new budget spending for Canadian infrastructure protection is marked at USD 144.9 million over five years, including Canada's critical cyber systems, which span the finance, telecommunications, energy, and transport industries, further driving the demand for embedded security solutions.
- The Health Insurance Portability and Accountability Act, a federal statute of the United States, reported an increase of 25% annually in data breaches in the Healthcare Data Breach Report, with 29,298,012 healthcare records in total breached. Such increases are projected to drive the market studied.
Embedded Security Industry Overview
The embedded security market is highly fragmented, and major players have used various strategies, such as new product launches, expansions, agreements, partnerships, and acquisitions, to increase their footprints in this market. Such developments result in an intense rivalry in the market. Key players include Infineon Technologies AG and STMicroelectronics NV.
In March 2024, Monta Vista Software LLC, a company offering commercial embedded Linux solutions, announced the release of CG X 5.0. This significant 15th iteration of the carrier-grade Linux product line highlights Monta Vista's dedication to secure dependable and creative embedded systems development by introducing a number of advanced security improvements and updates.
In February 2024, LDRA, the leading inventor in embedded systems and technology, announced the much-anticipated return of the embedded safety and security summit (ESSS) as a physical event across India during the month of July 2024.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Study Assumptions
- 1.3 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Growing IoT Applications Increasing the Need for IoT Security
- 4.2.2 Adoption of Wearable Devices in Healthcare
- 4.3 Market Restraints
- 4.3.1 Low Demand Due to Impact of COVID-19
- 4.3.2 Non-adherence to Government Regulations Due to Lack of Auditing
- 4.4 Industry Value Chain Analysis
- 4.5 Industry Attractiveness - Porter's Five Forces
- 4.5.1 Threat of New Entrants
- 4.5.2 Bargaining Power of Buyers/Consumers
- 4.5.3 Bargaining Power of Suppliers
- 4.5.4 Threat of Substitute Products
- 4.5.5 Intensity of Competitive Rivalry
5 MARKET SEGMENTATION
- 5.1 Component Type
- 5.1.1 Hardware
- 5.1.2 Software
- 5.1.3 Service
- 5.2 Application
- 5.2.1 Payment
- 5.2.2 Authentication
- 5.2.3 Content Protection
- 5.2.4 Other Applications
- 5.3 End User
- 5.3.1 Automotive
- 5.3.2 Healthcare
- 5.3.3 Consumer Electronics
- 5.3.4 Telecommunications
- 5.3.5 Aerospace & Defence
- 5.3.6 Other End Users
- 5.4 Geography
- 5.4.1 North America
- 5.4.1.1 United States
- 5.4.1.2 Canada
- 5.4.2 Europe
- 5.4.2.1 Germany
- 5.4.2.2 United Kingdom
- 5.4.2.3 France
- 5.4.2.4 Rest of Europe
- 5.4.3 Asia-Pacific
- 5.4.3.1 India
- 5.4.3.2 China
- 5.4.3.3 Japan
- 5.4.3.4 Rest of Asia-Pacific
- 5.4.4 Rest of the World
- 5.4.4.1 Latin America
- 5.4.4.2 Middle East and Africa
- 5.4.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Infineon Technologies AG
- 6.1.2 STMicroelectronics NV
- 6.1.3 Texas Instruments Inc.
- 6.1.4 McAfee LLC
- 6.1.5 Microchip Technology Inc.
- 6.1.6 Intellias Ltd
- 6.1.7 Karamba Security Ltd
- 6.1.8 Samsung Electronics Co.
- 6.1.9 Idemia Group
- 6.1.10 Rambus Incorporated













