 |
市場調查報告書
商品編碼
1267285
流媒體盜版市場和生態系統戰略Streaming Piracy Market & Ecosystem Strategies |
||||||
價格
簡介目錄
這份報告審視了流媒體盜版市場,全面介紹了盜版威脅和對策的演變,並對美國視頻服務提供商的收入損失進行了五年預測。
內容
定義:什麼是盜版?
關鍵問題和研究方法
執行摘要
消費者對版權侵權的態度
- 消費者洞察
- 消費者參與版權侵權
- 打算在未來 6 個月內訂閱電視服務
- 使用的版權侵權工具
- 消費者參與版權侵權和帳戶共享
- 提供和接收帳戶憑據的家庭的平均百分比
- 在 OTT 服務商業模式中使用盜版工具
- 強烈同意使用未經授權的視頻媒體
- 降價對盜版工具用戶的影響
防止版權侵權的原因
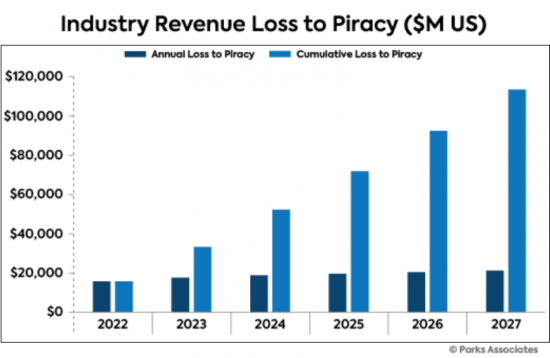
- 版權侵權造成的收入損失,所有美國家庭(百萬美元)
- 視頻資產生命週期
- 現場活動:價值下降
- 安全目的
- 關鍵安全原理
- 保護我們的聲譽並打擊盜版
- 降低盜竊風險並保持收入
- 消費者參與版權侵權和帳戶共享
- 版權侵權的其他消費者渠道
- 履行我們的義務並維護我們廣告的誠信和聲譽
- 優化分發
盜版生命週期:識別版權侵權
盜版的生命週期:盜版獲取
盜版生命週期:分發
盜版生命週期:檢測和威懾
盜版的生命週期:緩解和參與
盜版生態系統方法
其他版權侵權用例
預測版權侵權
- 市場驅動因素和障礙
- 美國流媒體視頻家庭(百萬戶)
- 每個美國家庭的流媒體收入(百萬美元)
- 流媒體收入 - 每個美國家庭(100 萬美元)
- 盜版率,佔流媒體收入的百分比
- 盜版造成的年收入損失,每個美國家庭(美元)
- 版權侵權造成的收入損失,所有美國家庭(百萬美元)
- 按視頻類型劃分的每月收入損失(百萬美元)
- 按視頻類型劃分的年收入損失(百萬美元)
- 電視盜版,按節目類型分類
- 網絡和移動設備上的欺詐性廣告 - 2022 年至 2027 年(百萬美元)
- 網絡和移動廣告欺詐明細(百萬美元)
附錄:主要供應商
附錄:定義
附錄:版權侵權參考
附錄:研究方法
簡介目錄
SYNOPSIS:
This study provides a comprehensive view of piracy threats and the evolution of anti-piracy techniques along with five-year forecasts of revenue loss in the US market for video service providers.

ANALYST INSIGHT:
"Piracy is increasingly being seen as an ecosystem-level threat, global in scope, to be fought by orchestrating theft-recognition, antipiracy countermeasures, best-practices, and collaboration across industry, law enforcement and government," said Steve Hawley, Contributing Analyst, Parks Associates.
Table of Contents
Definition: What is piracy?
Key questions and research approach
Executive Summary
- Industry insights
- Key findings: The impact of piracy
- The piracy-antipiracy life cycle
Consumer Attitudes Toward Piracy
- Consumer insights
- Consumer engagement with piracy
- Intention of Subscribing to a TV Service in Next 6 Months
- Piracy Tool Used
- Consumer Engagement in Piracy and Account Sharing
- Average Percentage of Households Giving or Receiving Account Credentials
- Pirate Tool Usage in OTT Service Business Models
- Strong Agreement Towards Unlicensed Video Media Usage
- Impact of Lower Pricing on Pirating Tool Users
Why Protect Against Piracy?
- Revenue Loss to Piracy, All US Households ($M US)
- Lifecycle of a Video Asset
- Live Events: Decline in Value
- The purpose of security
- Key rationale for security
- Protecting reputation and fighting piracy
- Reducing the risk of theft, preserving revenue
- Consumer Engagement in Piracy and Account Sharing
- Additional consumer-facing paths to piracy
- Meeting obligations, maintaining advertising integrity, and preserving reputation
- Optimizing distribution
Piracy Life Cycle: Recognizing Piracy
- The piracy-antipiracy life cycle: Recognition of piracy
- Piracy orders of magnitude
- The piracy ecosystem, from a distributor's perspective
Piracy Life Cycle: Acquisition by Pirates
- The piracy-antipiracy life cycle: Acquisition of content and services by pirates
- Where theft occurs, from a video distributor's perspective
- Pirates steal services and content
- Pirates compromise service delivery infrastructure, devices and software
- Pirates exploit consumer access
- Pirates exploit a variety of alternatives to capture content
- Pirates profiting from stolen (legitimate) advertising
- Pirates profit from fraudulent advertising (malvertising)
- Close-up: examples of ransomware ads
Piracy Life Cycle: Distribution
- The piracy-antipiracy life cycle: distribution
- Consumer-to-consumer distribution: it's not piracy if it's allowed by rights-holder
- Business-to-consumer distribution by pirates
- Online distribution: peer-to-peer (P2P)
- Online distribution: live streaming
- Online distribution: media centers and app stores as hosts to pirate apps
- Online distribution: compromised devices
- Online distribution: illicit streaming devices (ISDs)
- Online distribution: retail "IPTV" services
- IPTV business models: consumer-facing offers
- Setting up a piracy operation: choose a service platform and back-end
- Close-up: the profits from piracy far outweigh the costs
- Piracy business models: piracy-as-a-service
- Piracy-as-a-service: outsource the entire operation, including the content
Piracy Life Cycle: Detection & Deterrence
- The piracy-antipiracy life cycle: Piracy detection and deterrence
- Piracy deterrence: pay TV and streaming security
- Pay-TV antipiracy: detection through watermarking & monitoring
- Piracy deterrence: platform requirements for usage monitoring and analytics
- Piracy deterrence: protecting apps from penetration and reverse engineering
- Piracy deterrence: service parameters and administration practices
- Piracy deterrence: best practices for service administration
- Piracy deterrence: conceptual guidelines
- Piracy deterrence: business rules should guide detection parameters
- Summary: components of an antipiracy framework
Piracy Life Cycle: Mitigation and Engagement
- The piracy-antipiracy life cycle: mitigation & ecosystem engagement
- Piracy mitigation: end-user mitigation practices and infrastructure and network issues
- Piracy mitigation: operations and vendor administration
- Ongoing deterrence: operations practices and countermeasures
Ecosystem Approaches Against Piracy
- Non-technical countermeasures: ecosystem engagement
- Industry collaborations against piracy: Americas
- Antipiracy approaches differ region-to-region
Additional Piracy Use Cases
- Cases: illegal distribution via 'IPTV' sites and illicit streaming devices (ISDs)
- Cases: ransomware / piracy-as-a-service
- Cases: VASTFLUX - exploiting ad automation by fraud
- Cases: antipiracy through collaboration
Piracy Forecast
- Market drivers and barriers
- US Streaming Video Households (Millions)
- US Streaming Revenue per Household ($US)
- Streaming revenue - All US Households ($M)
- Piracy Rate, Percentage of Streaming Revenue
- Annual Revenue Loss to Piracy, per US HH ($US)
- Revenue Loss to Piracy, All US HH ($M US)
- Monthly Revenue Loss by Video Type ($M US)
- Annualized Revenue Loss by Video type ($M US)
- TV Piracy by Programming Type
- Fraudulent Advertising to Web and Mobile - 2022-2027 ($M)
- Breakout of Ad Fraud between Web and Mobile ($M)
Appendix: Key Suppliers
- Core security / antipiracy suppliers and their security categories
- Leaders in antipiracy products and solutions
Appendix: Definitions
Appendix: Piracy Reference
Appendix: Methodology
02-2729-4219
+886-2-2729-4219










