 |
市場調查報告書
商品編碼
1630210
文件完整性監控:市場佔有率分析、產業趨勢/統計、成長預測(2025-2030)File Integrity Monitoring - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
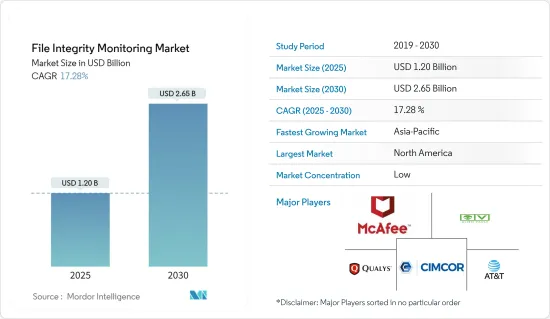
文件完整性監控市場規模預計到 2025 年為 12 億美元,預計到 2030 年將達到 26.5 億美元,預測期內(2025-2030 年)複合年成長率為 17.28%。
文件完整性監控市場允許組織以安全的方式測試和檢查作業系統(OS)、資料庫和應用程式軟體文件,以確保文件、照片、影片和文件沒有被篡改或損壞。組織正在採用這些技術,使員工能夠儲存、存取、管理和確保資料安全,而無需使用消費群的文件共用應用程式或軟體。
主要亮點
- 例如,企業工作站主要使用 Windows、Mac OS 和 Linux OS。另一方面,員工使用平板電腦和智慧型手機等行動設備,其中 Android 和 iOS 是主要作業系統。雲端服務的激增和活動目錄使用者的激增使得管理員很難控制授予組織內人員的權利和特權。結果,漏洞增加,這對您的組織來說可能是災難性的。
- 文件完整性監控已成為簡化管理員流程並應對組織當今面臨的網路威脅的重要工具。文件完整性監控解決方案還負責監控共用文件活動並向管理員提供及時警報以最大程度地減少威脅。
- 文件完整性監控市場解決的關鍵問題是特權濫用。濫用特權是指網路策略中的使用者未更新且該使用者的憑證被用來存取和變更檔案。
- 文件監控和完整性管理解決方案的格局正在迅速變化。以前,系統管理員手動授予存取權限並檢查漏洞。儘管如此,隨著事件數量的增加,管理員無法識別威脅。因此,來自 Netwrix、Lepide 和 Dell 的解決方案應運而生,為市場提供獨立的解決方案。然而,這些解決方案限制了用戶數量並管理許多事件。
- 卡巴斯基和McAfee等防毒供應商已經意識到這一附加安全層的重要性,並將其整合到他們的防毒解決方案中。然而,IBM 和 SolarWinds 等公司擁有滿足大型企業需求的解決方案,並擁有識別誤報的先進技術,以清理發送給管理員的通知。
- 在 COVID-19 爆發期間,許多國家的網路威脅呈上升趨勢。例如,澳洲網路安全中心(ACSC)已宣佈在疫情期間防範網路攻擊。各國進一步加強加強文件完整性監控系統。
- 在 COVID-19 大流行期間,網路安全已成為重中之重。人們越來越依賴數位技術來維持文件完整性監控流程的運作。此外,根據美國勞工統計局 (BLS) 的數據,從 2022 年到 2032 年,資訊安全分析師的就業人數預計將增加 32%,明顯快於所有職業的平均值。
文件完整性監控市場趨勢
BFSI產業預計將經歷最高成長
- 由於其廣泛的基本客群和金融資訊的重要性,BFSI 行業是遭受資料外洩和網路攻擊的關鍵基礎設施領域之一。與其他行業相比,金融服務機構受到網路攻擊的可能性高出四倍,預計這將推動對此類解決方案的需求。
- 此外,根據安全提供者 Bit Defender 的說法,目前銀行機構基於活動目錄的駭客攻擊最為普遍。此外,安全機構發出的各種警告進一步強調了監控文件完整性的必要性。
- 安全機構指出,lockerGoga 勒索軟體等勒索軟體和 APT15(也稱為 K3chang、Mirage、Vixen Panda、GREF 和 Playful Dragon)等駭客組織是攻擊 BFSI 機構活動目錄的最常見形式。
- 此外,資料外洩可能導致成本飆升和有價值的客戶資訊遺失。例如,2023 年 6 月,EpiSource LLC 發現其 Amazon Web Services 環境中的可疑活動導致未授權存取敏感客戶資料後,向加州總檢察長辦公室提出了資料外洩投訴(我已通知您)。此外,2023年5月,美國聯邦貿易委員會宣布亞馬遜將因侵犯隱私而支付兩項罰款:因未刪除兒童資料而罰款2,500萬美元;因限制存取安全影片而罰款580萬美元。
- 為了保護 IT 流程和系統、保護關鍵客戶資料並遵守政府法規,私人和公共銀行機構正在專注於實施最新技術來防止網路攻擊。此外,客戶期望的提高、技術力的提高以及監管要求的收緊,迫使銀行機構採取積極主動的安全措施。
亞太地區成長迅速
- 預計亞太地區很快就會為市場提供利潤豐厚的機會。不斷成長的行業日益成長的安全需求、保護組織中高價值目標的需要以及法規遵從性等因素正在推動該地區採用文件完整性監控解決方案。
- 亞太地區的中小型企業正在從傳統的本地環境過渡到混合雲端環境。這是因為混合雲環境帶來了可擴充性和安全性問題。
- 亞太國家正被用作網路攻擊的發射台,作為不安全基礎設施的脆弱溫床,大量電腦很容易受到大規模攻擊的感染,或作為全球連接的單點存取點。因此,該地區對文件完整性監控系統的需求正在增加。
- 中國備受爭議的網路安全法(CSL)旨在透過新法律保護中國的網路和個人用戶資訊。這包括電力和公共產業、交通服務、金融機構,以及作為「關鍵」部門主要供應商或持有大量中國公民資訊的外國公司,因此市場需求正在增加。
文件完整性監控產業概述
文件完整性監控市場是分散的,同一市場中的大多數全球參與者都在採取措施,透過專注於產品多樣化和開發來擴大其市場佔有率。該市場的主要企業包括 AT&T、McAfee LLC、Qualys Inc.、AlienVault Inc. 和 Cimcor Inc.。
2023 年 8 月,全球IT安全公司 LogRhythm 與美國安全、完整性和合規性軟體解決方案供應商 Cimcor 宣佈建立合作夥伴關係,共同開發創新的安全和完整性軟體解決方案。透過將Cimcor 的文件完整性監控(FIM) 解決方案CimTrak 與LogRhythm 的全面安全資訊和事件管理(SIEM) 平台結合,兩家公司將攜手合作,幫助世界各地的組織提高可見性,並協助保護您免受最新的網路攻擊。
IT安全與合規平台供應商 Qualis 將於 2023 年 2 月發布其 GovCloud 平台,並表示該平台在高影響力等級上符合 FedRAMP 嚴格的網路安全保證要求。聯邦機構可以使用 Qualys 的 GovCloud 平台來開發和實施網路安全計畫。 GovCloud 的功能之一包括檔案完整性監控,它符合 NIST SI-7 要求,並通知最終用戶對軟體、韌體和資訊進行詐欺的更改。
其他好處:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第1章簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場洞察
- 市場概況
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 買家/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭公司之間敵對關係的強度
- 產業價值鏈分析
- 評估 COVID-19 對文件完整性監控市場的影響
第5章市場動態
- 市場動態介紹
- 市場促進因素
- 資料安全威脅日益增加
- 對組織資料管理和人為錯誤檢測的需求不斷成長
- Microsoft OS AD 基礎架構中的漏洞
- 市場限制因素
- 財務限制和創新成本高
第6章 市場細分
- 按組織規模
- 小型企業
- 主要企業
- 依部署類型
- 本地
- 雲
- 依部署方式
- 代理基地
- 雲
- 按最終用戶產業
- 零售
- BFSI
- 款待
- 衛生保健
- 政府機構
- 娛樂
- 其他最終用戶產業
- 地區
- 北美洲
- 歐洲
- 亞太地區
- 拉丁美洲
- 中東/非洲
第7章 競爭格局
- 公司簡介
- McAfee, LLC
- AlienVault, Inc.
- Cimcor, Inc.
- Qualys, Inc.
- AT&T
- SolarWinds Worldwide, LLC
- LogRhythm, Inc.
- New Net Technologies LLC
- Trend Micro Inc.
- TrustWave Holdings, Inc.
- Ionx Solutions LLP
- Splunk Technology
- Software Diversified Services
- IBM Corporation
- Securonix Inc.
第8章投資分析
第9章 市場的未來
The File Integrity Monitoring Market size is estimated at USD 1.20 billion in 2025, and is expected to reach USD 2.65 billion by 2030, at a CAGR of 17.28% during the forecast period (2025-2030).

The file integrity monitoring market is a service that enables organizations to test and check operating system (OS), database, and application software files to determine whether or not they have been tampered with or corrupted documents, photos, videos, and files in a secure manner. Organizations adopt these technologies to help employees avoid using consumer-based file-sharing applications and software to store, access, and manage to ensure data security.
Key Highlights
- For instance, enterprises' workstation dominantly uses Windows, Mac OS, and Linux OS. In contrast, their employees utilize mobile devices like tablets and smartphones, with Android and iOS as the dominant operating systems. Due to the widespread adoption of cloud services and an increasing number of active directory users, admins find it difficult to manage privileges and rights granted to the people inside the organization. This has led to an increased vulnerability, which could be disastrous for the organization.
- File integrity monitoring eases the admin process and has been a critical tool in combating cyber threats organizations have recently faced. File integrity monitoring solution monitors the activity of the shared files and is also responsible for timely alerting the admin to minimize the threats.
- The key issue that the file integrity monitoring market resolves is privilege abuses. Privilege abuse is when the policies of the user within the network are not updated, due to which the user's credentials are used to access the files and then make changes to them.
- The landscape of file monitoring and integrity management solution has been changing rapidly. Earlier, the systems admin used to manually grant access and check for vulnerabilities. Still, as the number of events increased, it became impossible for the admins to identify the treats. This gave rise to Netwrix, Lepide, and Dell solutions, which offered standalone solutions for the market. However, these solutions limited the number of users and managed many events.
- The antivirus providers, like Kaspersky and McAfee, realized the importance of this additional layer of security and integrated the solution into their antivirus solutions. However, companies like IBM and SolarWinds have solutions that meet large enterprises' requirements and have advanced methodologies to identify false positives to declutter the notifications sent to the admins.
- During the outbreak of COVID-19, cyber threats were on the rise in numerous countries. For instance, the Australian Cyber Security Centre (ACSC) announced protecting itself from cyberattacks amid the pandemic. Various countries further enhanced their efforts to increase file integrity monitoring systems.
- Cybersecurity became a top priority during the global COVID-19 pandemic. There was an increasing dependence on digital technologies to keep the file integrity monitoring process running. Moreover, according to the US Bureau of Labor Statistics (BLS), from 2022 to 2032, information security analyst employment is expected to grow by 32%, substantially faster than the average for all occupations.
File Integrity Monitoring Market Trends
BFSI Industry is Expected to Witness The Highest Growth
- The BFSI sector is one of the critical infrastructure segments that suffer several data breaches and cyberattacks, owing to the large customer base that the industry serves and the financial information that is at stake. Financial service institutions have been identified to be four times more susceptible to cyberattacks when compared to other industries, which is expected to drive the demand for such solutions.
- Moreover, active directory-based hacking on banking institutions has become the most prevalent recently, according to security provider Bit defender. Also, the need for file integrity monitoring is further emphasized by different warnings sent out by security agencies.
- The security agencies have identified ransomware, like lockerGoga ransomware, and hacking groups, like APT15 - aka K3chang, Mirage, Vixen Panda, GREF, and Playful Dragon, have been most prevalent in attacking the active directory of the BFSI institutions.
- Furthermore, Data breaches lead to an exponential rise in costs and the loss of valuable customer information. For instance, in June 2023, EpiSource LLC notified the Attorney General of California of the data breach after identifying that unauthorized access to sensitive customer data had occurred due to suspicious activity in the company's Amazon Web Services environment. Additionally, in May 2023, the Federal Trade Commission announced that Amazon would pay two distinct fines for privacy violations: USD 25 million for allegedly failing to delete children's data and USD 5.8 million for limiting access to Ring security videos for employees and contractors.
- To secure their IT processes and systems, secure critical customer data, and comply with government regulations, private and public banking institutes focus on implementing the latest technology to prevent cyber attacks. Additionally, with greater customer expectations, increasing technological capabilities, and regulatory requirements, banking institutions are pushed to adopt a proactive approach to security.
Asia-Pacific to Witness Fastest Growth
- Asia-Pacific is estimated to present lucrative opportunities for the market shortly. Factors such as the increased need for security in growing industries, the need to protect high-value targets in organizations, and regulatory compliance are driving the adoption of file integrity monitoring solutions in the region.
- Small and medium-sized businesses are transforming into a hybrid cloud environment in Asia-Pacific from the legacy on-premise environment. Numerous factors have triggered this, as the hybrid cloud environment provides scalability and security concerns.
- Asia-Pacific countries are being used as launchpads for cyber attacks, either as vulnerable hotbeds of unsecured infrastructures where numerous computers can be infected easily for large-scale attacks or as centers for a single point of attack to gain access to the hubs' global connections. So the demand for file integrity monitoring systems is rising in this region.
- China's controversial Cyber Security Law (CSL) is aimed at protecting China's networks and private user information with a new law. It includes power and utility providers, transportation services, and financial institutions, including any foreign company that is a key supplier to a 'critical' sector or holds significant amounts of information on Chinese citizens, increasing the market demand in this country.
File Integrity Monitoring Industry Overview
The file integrity monitoring market is fragmented as the vast majority of the global players functioning in the market are taking steps to raise their market footprint by concentrating on product diversification and development. Some of the key players in the market are AT&T, McAfee LLC, Qualys Inc., AlienVault Inc., and Cimcor Inc., among others.
In August 2023, LogRhythm, a global IT security company, and Cimcor, a United States-based security, integrity, and compliance software solutions provider, announced a partnership to develop innovative security and integrity software solutions. Combining Cimcor's file integrity monitoring (FIM) solution, CimTrak, with LogRhythm's comprehensive security information and event management (SIEM) platform, the two companies work together to help organizations all over the world increase visibility and protect against modern cyberattacks.
In February 2023, Qualys, a provider of IT security and compliance platforms, released its GovCloud platform, which it states meets the stringent cybersecurity assurance requirements of FedRAMP at the high impact level. Federal agencies can use Qualys' GovCloud platform to develop and implement cybersecurity programs. One of GovCloud's features includes File Integrity Monitoring, which notifies end users about unauthorized changes to software, firmware, and information in compliance with NIST SI-7 requirements.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Industry Value Chain Analysis
- 4.4 Assessment of COVID-19 Impact on the File Integrity Monitoring Market
5 MARKET DYNAMICS
- 5.1 Introduction to Market Dynamics
- 5.2 Market Drivers
- 5.2.1 Increasing Threats to Data Security
- 5.2.2 Increasing Need to Control Organization Data and Spot Human Errors
- 5.2.3 Vulnerabilities in AD Infrastructure of Microsoft OS
- 5.3 Market Restraints
- 5.3.1 Financial Constraints and High Innovation Costs
6 MARKET SEGMENTATION
- 6.1 By Organization Size
- 6.1.1 Small and Medium Enterprises
- 6.1.2 Large Enterprises
- 6.2 By Deployment Type
- 6.2.1 On-Premise
- 6.2.2 Cloud
- 6.3 By Installation Mode
- 6.3.1 Agent-Based
- 6.3.2 Cloud
- 6.4 By End-user Industry
- 6.4.1 Retail
- 6.4.2 BFSI
- 6.4.3 Hospitality
- 6.4.4 Healthcare
- 6.4.5 Government
- 6.4.6 Entertainment
- 6.4.7 Other End-user Industries
- 6.5 Geography
- 6.5.1 North America
- 6.5.2 Europe
- 6.5.3 Asia-Pacific
- 6.5.4 Latin America
- 6.5.5 Middle East & Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 McAfee, LLC
- 7.1.2 AlienVault, Inc.
- 7.1.3 Cimcor, Inc.
- 7.1.4 Qualys, Inc.
- 7.1.5 AT&T
- 7.1.6 SolarWinds Worldwide, LLC
- 7.1.7 LogRhythm, Inc.
- 7.1.8 New Net Technologies LLC
- 7.1.9 Trend Micro Inc.
- 7.1.10 TrustWave Holdings, Inc.
- 7.1.11 Ionx Solutions LLP
- 7.1.12 Splunk Technology
- 7.1.13 Software Diversified Services
- 7.1.14 IBM Corporation
- 7.1.15 Securonix Inc.









