 |
市場調查報告書
商品編碼
1637853
製造業雲端安全:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)Cloud Security in Manufacturing - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
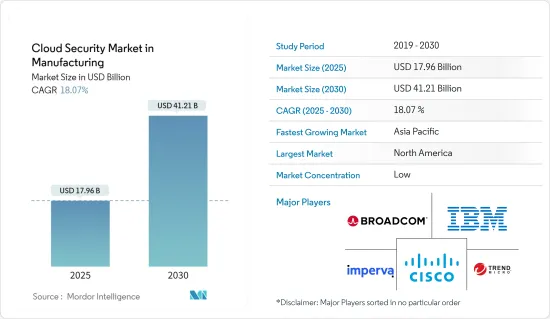
製造業雲端安全市場預計將從 2025 年的 179.6 億美元成長到 2030 年的 412.1 億美元,預測期內(2025-2030 年)的複合年成長率為 18.07%。
製造業正在快速發展,推動對敏捷系統創新和流程支援的需求。這種需求推動了雲端安全解決方案的採用,為製造商提供了更高的可視性和靈活性。
主要亮點
- 製造業是網路攻擊最嚴重的行業之一,大約一半的製造商都經歷過網路安全事件。這導致了重大的財務損失和業務營運的中斷。因此,企業預算的很大一部分都花在了安全解決方案上。
- 然而,目前大多數生產流程都由內部部署解決方案支持,因此將生產流程從內部部署遷移到雲端是一項艱鉅的挑戰。製造公司應該專注於可以遷移到雲端的新事件,同時開發更智慧的 ERP 系統來處理舊事件,從而使製造能力可以根據需要擴展。
- 世界各國政府正透過官民合作關係關係投資雲端基礎運算的交付方式,為創新大都會企業和智慧交通網路提供支援。雲端基礎的技術提供了可靠、經濟且可擴展的成果,將大都市轉變為數位連接的智慧結構。在整個中東地區,各國政府都在支持發展智慧城市和創新交通服務的舉措,例如杜拜網路城 (DIC) 和沙烏地阿拉伯王國 (KSA) 的「2030 願景」。
- 此外,2023 年 7 月,Sight Machine Inc. 宣布其製造資料平台現已成為 Microsoft Cloud for Manufacturing 的認證解決方案,進一步擴大了其在 Microsoft Azure 市場中的影響力。 SiteMachine 多年來一直參與微軟的製造合作夥伴生態系統,這將使該公司能夠利用雲端、資料和人工智慧等先進技術,幫助世界各地的製造商轉變業務並達到新的生產力永續性。
- 然而,由於對雲端服務供應商 (CSP) 缺乏信任,大大小小的企業可能不願意將業務遷移到雲端。由於 CSP 掌握關鍵資料,因此它們很容易受到複雜的網路攻擊,這可能會使企業不願意將其非公開資料委託給這些提供者。
- 由於網路釣魚犯罪的增加,COVID-19 疫情導致了對雲端解決方案(包括雲端安全解決方案)的需求增加。詐騙利用新冠肺炎疫情作為誘餌來賺錢,而遠距工作模式的轉變使得臨時工詐騙計畫更容易實施,因為通訊在很大程度上依賴於臨時工作。
- 總而言之,受網路威脅、對更高靈活性的需求以及系統創新和流程支援的可見性的推動,製造業對雲端安全解決方案的採用預計將快速成長。此外,儘管對 CSP 的信任問題仍然是一個挑戰,但政府對雲端基礎的技術的投資也可能促進市場成長。 COVID-19 疫情凸顯了雲端安全解決方案的重要性。
雲端安全市場趨勢
入侵偵測和預防是成長最快的領域
- 入侵偵測和預防軟體 (IDPS) 是一種監控網路流量以發現潛在攻擊徵兆的安全系統。其主要目的是識別潛在的危險活動並立即採取行動防止攻擊。這可能包括丟棄惡意資料包、阻止網路流量或重置連線。此外,IDPS 通常會向安全管理員發送警報,告知他們潛在的威脅。
- 數位孿生是使用物聯網 (IoT)資料創建的實體物件、環境和流程的虛擬表示。數位雙胞胎使製造商能夠透過在虛擬環境中模擬和分析資料來最佳化產品、流程和決策。在整個資料生命週期中連接和管理資料的方法稱為數位執行緒。
- 隨著IT效能的提高,製造商可以利用基於IT的模擬、建模和資料分析來最佳化其對各種應用情境的反應。高效能運算 (HPC) 功能(包括複雜運算、提高的營運靈活性和更好地利用 IT 資源)是此最佳化過程中使用的標準工具。 HPC 系統用途極為廣泛,廣泛應用於製藥、離散製造和製程製造等許多不同領域。
- 數位工程利用雲端基礎的製造資料工具和相容的合作夥伴解決方案生態系統,幫助製造商加速其產品開發流程。
- IDS 或 IPS 系統的成功部署和運作取決於兩個主要因素:部署的特徵碼和通過它的網路流量。全面且定期更新的簽章資料庫可確保系統能準確偵測潛在威脅。流經系統的網路流量是一級資訊來源,系統必須能夠即時處理和分析它。
亞太地區將經歷最高成長
- 亞太地區目前是全球成長最快的地區。根據《東協郵政》報道,製造業是東南亞國家聯盟(東協)經濟成長的主要動力。
- 推動這一成長的關鍵舉措之一是東協經濟共同體 (AEC),旨在將東協建立為單一市場和生產中心。此外,區域全面經濟夥伴關係(RCEP)等大型貿易協定可能是建立更廣泛的亞太自由貿易區(FTAAP)的重要一步,為促進自由貿易提供寶貴工具。
- 為了幫助亞太地區 (APAC) 的企業防範和應對日益嚴重的網路攻擊威脅,IBM 宣布對網路安全資源進行大量投資。這項投資將以 IBM 安全指揮中心為特色,該中心將運行高度逼真的網路攻擊模擬,並為從技術執行長到高階主管層的每個人提供應對技術的培訓。
- 作為這項投資的一部分,IBM 還將收購一個全新的安全營運中心 (SOC),該中心將整合到公司廣泛的全球 SOC 網路中,為全球客戶提供全天候安全回應服務。
- 許多領先的公司正在擴大在亞太地區的業務。例如,Google最近將其亞太地區的 Google Cloud Platform 區域從三個擴展到六個。
雲端安全產業概覽
由於對網路攻擊的擔憂日益加劇,製造業雲端安全市場高度分散。許多公司正在擴展其服務以適應各種規模的組織。該市場的一些主要企業包括思科系統公司、IBM 公司、博通和 Imperva。
- 2023 年 4 月 – AWS 推出製造業和工業能力。 AWS 已宣布推出 AWS 製造和工業能力。 AWS 製造和工業能力擴展了類別,以進一步區分合作夥伴並協助客戶找到適合其共同業務需求的解決方案。
- 2022 年 5 月-雲端運算產業最大公司Google宣布推出針對智慧工廠和智慧員工的全新Google雲端製造 (Google Cloud Manufacturing)。 Google Cloud 的新製造解決方案使製造工程師和工廠經理能夠存取來自所有不同資產和流程的統一、情境化的資料。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 調查結果
- 調查前提
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場動態
- 市場概況
- 市場促進因素與限制因素簡介
- 市場促進因素
- 網路威脅日益加劇推動市場擴張
- 市場限制
- 將製造流程從本地遷移到雲端是一項重大挑戰
- 價值鏈分析
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 購買者/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭強度
第5章 市場區隔
- 按解決方案
- 身分和存取管理
- 預防資料外泄
- IDS/IPS
- 安全資訊和事件管理
- 加密
- 安全
- 應用程式安全
- 資料庫安全
- 端點安全
- 網路安全
- Web 和電子郵件安全
- 依部署方式
- 民眾
- 私人的
- 混合
- 按地區
- 北美洲
- 歐洲
- 亞太地區
- 世界其他地區
第6章 競爭格局
- 公司簡介
- Trend Micro Inc.
- Imperva Inc.
- Broadcom Inc.
- IBM Corporation
- Cisco Systems Inc.
- Fortinet Inc.
- Sophos PLC
- Mcafee LLC
- Qualys Inc.
- Check Point Software Technologies Ltd
- Computer Science Corporation(CSC)
第7章投資分析
第8章 市場機會與未來趨勢
The Cloud Security Market in Manufacturing Industry is expected to grow from USD 17.96 billion in 2025 to USD 41.21 billion by 2030, at a CAGR of 18.07% during the forecast period (2025-2030).

The manufacturing industry is rapidly evolving, and with it comes an increasing demand for agile system innovation and process support. This demand has led to the adoption of cloud security solutions, which offer greater visibility and flexibility to manufacturers.
Key Highlights
- Manufacturing is one of the most highly targeted industries for cyberattacks, with almost half of all manufacturers have experienced a cybersecurity incident. This has resulted in significant financial losses and disruptions to business operations. As a result, a major portion of a company's budget is being spent on security solutions.
- However, migrating production processes from on-premise to the cloud can be challenging, as most production processes are currently supported by on-premise solutions. Manufacturers should focus on new events that can be transferred to the cloud while developing a more intelligent ERP system to handle older events, enabling manufacturing functions to scale as needed.
- Governments worldwide are investing in cloud-based computing delivery methods through public-private partnerships to advance innovative megacity enterprises and intelligent transportation networks. Cloud-based technology provides reliable, affordable, and scalable outcomes that can transform metropolises into digitally connected and intelligent structures. In the Middle East, governments are endorsing initiatives like the Dubai Internet City (DIC) and the Kingdom of Saudi Arabia (KSA) Vision 2030 to develop smart municipalities and innovative transportation services.
- Furthermore, in July 2023, Sight Machine Inc. announced that its Manufacturing Data Platform is now a certified solution for Microsoft Cloud for Manufacturing, further expanding its reach within the Microsoft Azure Marketplace. Sight Machine's multi-year participation in Microsoft's partner ecosystem for manufacturing enables organizations to assist manufacturers around the globe in transforming their businesses and unlock new levels of productivity and sustainability with leading cloud, data and AI-powered technology.
- However, large and small organizations may be hesitant to shift their operations to the cloud due to a lack of trust in cloud service providers (CSPs). CSPs hold critical data, making them highly vulnerable to complex cyberattacks that can discourage businesses from entrusting their nonpublic data to these providers.
- The COVID-19 pandemic increased the demand for cloud solutions, including cloud security solutions, due to an increase in phishing offenses. Scammers were using COVID-19 as a lure to generate income, and the shift to remote working made dispatch fraud schemes easier to execute as communication relies heavily on dispatch.
- In conclusion, the manufacturing industry's adoption of cloud security solutions is expected to grow rapidly, driven by cyber threats, demand for greater agility, and visibility in system innovation and process support. The government's investments in cloud-based technology will also contribute to market growth, though the issue of trust in CSPs remains a challenge. The COVID-19 pandemic highlighted the importance of cloud security solutions, which will continue to be in high demand in the foreseeable future.
Cloud Security Market Trends
Intrusion Detection and Prevention is the Fastest Growing Segment
- An intrusion detection and prevention software (IDPS) is a security system that monitors network traffic for any signs of potential attacks. Its primary purpose is to identify any potentially dangerous activity and take immediate action to prevent the attack. This may involve dropping malicious packets, blocking network traffic, or resetting connections. Additionally, the IDPS typically sends an alert to security administrators to inform them of the potential threat.
- Digital twins are virtual representations of physical objects, environments, and processes, created using data from the Internet of Things (IoT). Manufacturers can use digital twins to optimize their products, processes, and decisions by simulating and analyzing data in a virtual environment. The means of connecting and managing data throughout its lifecycle are known as digital threads.
- Manufacturers with improved IT performance can optimize their support for different application scenarios by leveraging IT-based simulations, modeling, and data analysis. High-performance computing (HPC) capabilities, such as complex calculations, greater operational agility, and better IT resource utilization, are standard tools used in this optimization process. HPC systems are incredibly versatile and widely used in various sectors, including pharmaceutical, discrete, and process manufacturing.
- Digital engineering, which involves utilizing cloud-based manufacturing data tools and an ecosystem of compatible partner solutions, can help manufacturers accelerate their product development process.
- The successful deployment and operation of an IDS or IPS system rely on two main factors - the deployed signatures and the network traffic that flows through it. A comprehensive and regularly updated database of signatures ensures that the system can accurately detect potential threats. The network traffic that flows through the system is the primary source of information, and the system must be capable of processing and analyzing it in real time.
Asia-Pacific to Witness the Highest Growth
- The Asia-Pacific region is currently experiencing the fastest growth in the world, thanks in large part to the expansion of its manufacturing sector. According to a report from the ASEAN Post, the manufacturing industry has been a crucial driver of economic growth for the Association of Southeast Asian Nations (ASEAN).
- One of the key initiatives driving this growth is the ASEAN Economic Community (AEC), which aims to establish ASEAN as a single market and production base. Additionally, mega trade agreements such as the Regional Comprehensive Economic Partnership (RCEP) could be a significant step towards the creation of a broader Free Trade Area of the Asia-Pacific (FTAAP), which would serve as a valuable intergovernmental forum for promoting free trade.
- To help businesses in the Asia Pacific (APAC) region prepare for and manage the growing threat of cyberattacks, IBM has announced a significant investment in its cybersecurity resources. The centerpiece of this investment is the IBM Security Command Center, which uses highly realistic simulated cyberattacks to teach response techniques to everyone from technical staff to the C-suite.
- As part of this investment, IBM has also acquired a brand-new Security Operation Center (SOC), which will be integrated into the company's extensive global network of SOCs to provide round-the-clock security response services to clients worldwide.
- Many major companies are expanding their presence in the APAC region. For example, Google has recently increased the number of Google Cloud Platform regions in APAC from three to six.
Cloud Security Industry Overview
The market for cloud security in the manufacturing industry has experienced fragmentation due to increasing concerns about cyberattacks. To cater to organizations of all sizes, many companies are expanding their services. Some of the significant players in this market include Cisco Systems Inc, IBM Corporation, Broadcom, and Imperva, among others.
- April 2023 - AWS announced the Manufacturing and Industrial Competency. AWS announced the launch of the AWS Manufacturing and Industrial Competency. The AWS Manufacturing and Industrial Competency has expanded to include the categories to further differentiate partners and assist customers in finding the right solution for their identical business needs.
- May 2022 - Google, the most prominent player in the cloud industry, introduced the new Google Cloud Manufacturing for smart factories and intelligent employees. Google Cloud's new manufacturing solutions allow manufacturing engineers and plant managers to access united and contextualized data from all their diverse assets and procedures.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Study Assumptions
- 1.3 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Growing Threats of Cyber Attacks is Expanding the Market
- 4.4 Market Restraints
- 4.4.1 Migration of Manufacturing Processes from On-premise to Cloud is a Major Challenge
- 4.5 Value Chain Analysis
- 4.6 Industry Attractiveness - Porter's Five Forces Analysis
- 4.6.1 Threat of New Entrants
- 4.6.2 Bargaining Power of Buyers/Consumers
- 4.6.3 Bargaining Power of Suppliers
- 4.6.4 Threat of Substitute Products
- 4.6.5 Intensity of Competitive Rivalry
5 MARKET SEGMENTATION
- 5.1 By Solution
- 5.1.1 Identity and Access Management
- 5.1.2 Data Loss Prevention
- 5.1.3 IDS/IPS
- 5.1.4 Security Information and Event Management
- 5.1.5 Encryption
- 5.2 By Security
- 5.2.1 Application Security
- 5.2.2 Database Security
- 5.2.3 Endpoint Security
- 5.2.4 Network Security
- 5.2.5 Web and Email Security
- 5.3 By Deployment Mode
- 5.3.1 Public
- 5.3.2 Private
- 5.3.3 Hybrid
- 5.4 By Geography
- 5.4.1 North America
- 5.4.2 Europe
- 5.4.3 Asia Pacific
- 5.4.4 Rest of the World
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Trend Micro Inc.
- 6.1.2 Imperva Inc.
- 6.1.3 Broadcom Inc.
- 6.1.4 IBM Corporation
- 6.1.5 Cisco Systems Inc.
- 6.1.6 Fortinet Inc.
- 6.1.7 Sophos PLC
- 6.1.8 Mcafee LLC
- 6.1.9 Qualys Inc.
- 6.1.10 Check Point Software Technologies Ltd
- 6.1.11 Computer Science Corporation (CSC)









