 |
市場調查報告書
商品編碼
1641855
威脅情報保全服務:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)Threat Intelligence Security Services - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
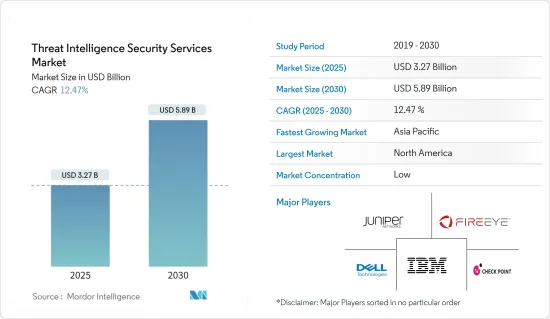
威脅情報保全服務市場規模預計在 2025 年為 32.7 億美元,預計到 2030 年將達到 58.9 億美元,預測期內(2025-2030 年)的複合年成長率為 12.47%。
主要亮點
- 保全服務提供者正在加強其威脅識別能力,以應對從進階持續性威脅(APT)到新型攻擊和新興惡意軟體的一系列挑戰。雖然出現了新的進階持續性威脅類別,但必須注意的是,這些威脅通常是由惡意軟體、網路釣魚等傳送系統和資料外洩的組合造成的。這些威脅的特徵是性質未知、目標有限、適應性強。
- 政府對資料安全的重視程度不斷提高、高級威脅的激增、雲端運算的興起、自帶設備 (BYOD) 模式的快速普及以及利用巨量資料分析獲取威脅情報等因素正在推動這一成長。市場成長。隨著無線運算和寬頻等技術的進步以及公司開發更先進的威脅情報解決方案,對威脅情報安全解決方案的需求只會增加。
- 此外,全球威脅情報安全市場預計將見證對網路流量分析、惡意軟體傳播器以及安全資訊和事件管理 (SIEM) 等工具的需求激增。
- 各種規模的組織擴大轉向託管服務來加強其網路安全態勢。除了提供主動保護之外,這些服務還有助於識別您組織的漏洞、推薦解決方案並提供一系列附加服務。
- 然而,該產業面臨威脅情報安全工具採購和實施成本高等挑戰,阻礙了該產業的成長軌跡。
威脅情報保全服務市場趨勢
網路安全事件快速增加推動市場
- 企業正在使用威脅情報安全工具來識別和打擊網路攻擊風險,推動全球市場趨勢。同時,公司正在轉向網路定義軟體和惡意軟體偵測工具來強化其 IT 系統。
- 而且,及時的威脅情報不僅可以幫助企業避免網路攻擊,還可以透過加強各級安全檢查來幫助企業從巨額財務損失中挽回損失,從而推動市場需求。
- 隨著新威脅瞄準設備和企業,物聯網社群和軟體開發人員正在轉向各種技術解決方案來減輕物聯網應用的網路風險。隨著越來越多的企業採用物聯網來提高生產力,網路犯罪分子將目標從傳統電腦轉移到物聯網設備。
- 威脅情報安全解決方案在防禦威脅和保護您的環境方面發揮著至關重要的作用。此外,由於 BYOD 模型的快速採用以及巨量資料分析與威脅情報安全框架的整合,這些解決方案的全球市場呈現出良好的投資前景。
亞太地區將經歷最高成長
- 預計亞太地區將在預測期內實現最高成長。這種快速成長的驅動力是技術進步、新興國家的崛起、安全意識的增強以及日益複雜的威脅。此外,該地區正逐漸融入正在進行的 IT 革命,並正在加大對科技的投資。
- 此外,該地區的成長受到技術進步、新興經濟體的崛起、對安全的日益重視以及不斷演變的威脅的推動。該地區與正在進行的 IT 革命的契合以及強勁的技術投資進一步推動了這一成長。
- 此外,資料庫量的突然增加、特權使用者帳戶和登入異常、非典型的網域名稱系統請求以及無法解釋的系統變更是這種成長的主要促進因素。
- 隨著企業面臨的網路安全漏洞風險越來越大,許多企業開始轉向威脅情報服務。隨著雲端平台、物聯網和其他網路技術的興起,這種變化尤其明顯。
威脅情報保全服務產業概況
威脅情報市場競爭激烈,由幾家大公司組成。從市場佔有率來看,目前市場主要被少數幾家大公司佔據。這些擁有突出市場佔有率的領先公司正致力於擴大海外基本客群,並利用策略合作措施來提高市場佔有率和盈利。
- 2023 年 10 月 Check Point 軟體技術有限公司(「Check Point」)今天宣布推出其全新的、預防優先的保全行動套件 Check Point。
- 2023 年 8 月 Fortinet 將推出首款 Secure SD 系列伺服器,該伺服器採用新的安全處理單元 5 (SP5) ASIC,以經濟實惠的價格提供業界領先的 AI 驅動的威脅預防效能、擴充性和能源效率。 - 推出FortiGate 90G 、WAN 設備和 NGFW。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 研究假設和市場定義
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場洞察
- 市場概況
- 價值鏈/供應鏈分析
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 購買者/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭
第5章 市場動態
- 市場促進因素
- 網路安全事件急劇增加
- M2M/IoT 連線的增加要求企業採取更強力的網路安全措施
- 市場限制
- 網路安全專家短缺
- 高度依賴傳統身分驗證方法且缺乏準備
第6章 市場細分
- 依部署方式
- 雲
- 本地
- 按最終用戶
- BFSI
- 衛生保健
- IT
- 零售
- 生命科學
- 按地區
- 北美洲
- 美國
- 加拿大
- 歐洲
- 德國
- 英國
- 法國
- 亞洲
- 中國
- 日本
- 韓國
- 澳洲和紐西蘭
- 拉丁美洲
- 中東和非洲
- 北美洲
第7章 競爭格局
- 供應商市場佔有率
- 公司簡介
- Juniper Networks Inc.
- Dell Inc.
- Check Point Software Technologies Ltd
- FireEye Inc.
- IBM Corporation
- AlienVault Inc.
- Farsight Security Inc.
- LogRhythm Inc.
- F-Secure Corporation
- Webroot Inc.
- Fortinet Inc.
- McAfee LLC
- Symantec Corporation
- LookingGlass Cyber Solutions Inc.
第8章 市場機會與未來趨勢
The Threat Intelligence Security Services Market size is estimated at USD 3.27 billion in 2025, and is expected to reach USD 5.89 billion by 2030, at a CAGR of 12.47% during the forecast period (2025-2030).

Key Highlights
- Security service providers are enhancing their threat identification capabilities to combat a range of challenges, from advanced persistent threats (APTs) to novel attacks and emerging malware. While a new category, the advanced persistent threat, has emerged, it is crucial to note that these threats often stem from a combination of malware, delivery systems like phishing, and data exfiltration. These threats are characterized by being unknown, low-targeted, and adaptive.
- Factors such as the increasing emphasis on data security by governments of various countries, a surge in advanced threats, widespread adoption of the cloud, the rapid adoption of bring-your-own-device (BYOD) models, and the utilization of big data analytics for threat intelligence are expected to propel the market's growth. As technologies like wireless computing and broadband advance and enterprises develop more sophisticated threat intelligence solutions, the demand for threat intelligence security solutions will only rise.
- Furthermore, the global threat intelligence security market is poised to witness a surge in demand for tools like network traffic analysis, malware dissemblers, and security information and event management (SIEM).
- Organizations, irrespective of size, are increasingly turning to management services to bolster their cybersecurity posture. These services not only provide proactive protection but also help identify organizational vulnerabilities, recommend solutions, and offer a suite of additional services.
- However, the industry faces challenges, notably in the form of high procurement and installation costs for threat intelligence security tools, which can impede its growth trajectory.
Threat Intelligence Security Services Market Trends
Rapidly Increasing Cyber Security Incidents to Drive the Market
- Enterprises utilize threat intelligence security tools to identify and combat cyber attack risks, bolstering global market trends. Concurrently, businesses are increasingly turning to network-defining software and malware detection tools to fortify their IT systems.
- Furthermore, timely threat intelligence not only averts cyber attacks but also aids in recovering significant financial losses as companies ramp up security checks across all levels, fueling market demand.
- As emerging threats target devices and enterprises, the IoT community and software developers are pivoting toward a diverse array of technology solutions to mitigate cyber risks in IoT applications. With a rising number of companies embracing IoT for heightened productivity, cybercriminals are shifting their focus from traditional computers to IoT devices.
- Threat intelligence security solutions play a pivotal role in preempting threats and safeguarding environments. Moreover, the global market for these solutions presents lucrative investment prospects, driven by the swift adoption of the BYOD model and the integration of big data analytics into threat intelligence security frameworks.
Asia-Pacific to Witness the Highest Growth
- Asia-Pacific is poised to achieve its peak growth during the forecast period. This surge is underpinned by technological advancements, the rise of new economies, heightened security awareness, and the escalating sophistication of threats. Additionally, the region is witnessing a deepening integration into the ongoing IT revolutions and increased investments in technology.
- Moreover, the region's growth is bolstered by technological advancements, the emergence of new economies, a growing emphasis on security, and an evolving threat landscape. This growth is further fueled by Asia-Pacific's alignment with the ongoing IT revolutions and its robust investments in technology.
- Furthermore, the upsurge in database volumes, anomalies in privileged user accounts and logins, atypical domain name system requests, and unexplained system changes are key drivers of this growth.
- As enterprises face heightened risks of cybersecurity breaches, many are turning to threat intelligence services. This shift is particularly pronounced due to the widespread adoption of cloud platforms, IoT, and other networking technologies.
Threat Intelligence Security Services Industry Overview
The threat intelligence market is highly competitive and consists of several major players. In terms of market share, few of the major players currently dominate the market. These major players, with prominent shares in the market, are focusing on expanding their customer base across foreign countries and are leveraging strategic collaborative initiatives to increase their market share and profitability.
- October 2023: Check Point Software Technologies Ltd announced the launch of Check Point Horizon Playblocks prevention-first security operations security suite, which includes the managed detection/prevention and response (MDR/MPR) SOC service, where it augments security by enabling products, people, and processes to work together to stop the proliferation of attacks.
- August 2023: Fortinet Inc. announced the FortiGate 90G, the first Secure SD-WAN appliance and NGFW with the new security processing unit 5 (SP5) ASIC that delivers industry-leading AI-powered threat protection performance, scalability, and power efficiency at a cost-effective price.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Value Chain / Supply Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Threat of New Entrants
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Bargaining Power of Suppliers
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Rapidly Increasing Cyber Security Incidents
- 5.1.2 Growing M2M/IoT Connections Demands for Strengthened Cyber Security in Enterprises
- 5.2 Market Restraints
- 5.2.1 Lack of Cyber Security Professionals
- 5.2.2 High Reliance on Traditional Authentication Methods and Low Preparedness
6 MARKET SEGMENTATION
- 6.1 By Deployment Mode
- 6.1.1 Cloud
- 6.1.2 On-premise
- 6.2 By End User
- 6.2.1 BFSI
- 6.2.2 Healthcare
- 6.2.3 IT
- 6.2.4 Retail
- 6.2.5 Life Sciences
- 6.3 By Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 Germany
- 6.3.2.2 United Kingdom
- 6.3.2.3 France
- 6.3.3 Asia
- 6.3.3.1 China
- 6.3.3.2 Japan
- 6.3.3.3 South Korea
- 6.3.4 Australia and New Zealand
- 6.3.5 Latin America
- 6.3.6 Middle East and Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Vendor Market Share
- 7.2 Company Profiles
- 7.2.1 Juniper Networks Inc.
- 7.2.2 Dell Inc.
- 7.2.3 Check Point Software Technologies Ltd
- 7.2.4 FireEye Inc.
- 7.2.5 IBM Corporation
- 7.2.6 AlienVault Inc.
- 7.2.7 Farsight Security Inc.
- 7.2.8 LogRhythm Inc.
- 7.2.9 F-Secure Corporation
- 7.2.10 Webroot Inc.
- 7.2.11 Fortinet Inc.
- 7.2.12 McAfee LLC
- 7.2.13 Symantec Corporation
- 7.2.14 LookingGlass Cyber Solutions Inc.












