 |
市場調查報告書
商品編碼
1651033
IAM保全服務:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)IAM Security Services - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
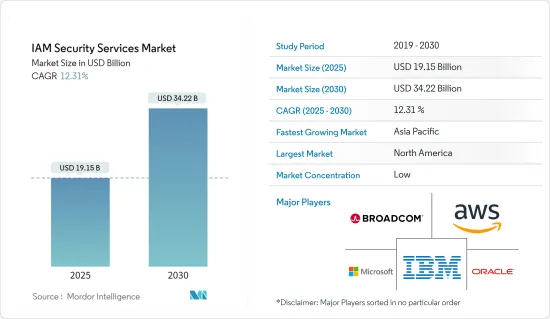
預計 2025 年 IAM保全服務市場規模為 191.5 億美元,到 2030 年將達到 342.2 億美元,預測期內(2025-2030 年)的複合年成長率為 12.31%。
主要亮點
- 身分和存取管理 (IAM) 確保根據工作角色或職能,適當的人員、軟體和硬體能夠存取執行其給定工作所需的工具。利用 IAM 的組織可以透過管理身分來簡化業務,而無需個人以管理員身分登入應用程式。
- 雲端技術正在透過成本效益和規模經濟改變業務開展方式。然而,缺乏有效的安全性會削弱雲端處理的優勢。這表明對包括身份相關犯罪在內的安全解決方案的基本需求,並正在推動 IAM 市場的發展。
- 透過使用 IAM 服務,企業不再需要本地 ID 供外部使用,應用程式管理也得到簡化,任何組織都可以透過 IAM 服務降低 IT 營運成本。雲端基礎的IAM 服務減少了購買和維護內部基礎設施的需要,進一步推動了市場採用。
- IAM 軟體讓公司完全控制其身分和內部網路的存取。企業可以實施可靠的密碼規則和雙重認證。這些功能可實現多因素身份驗證 (MFA),使企業安全性保持最新,並使公司能夠執行其安全策略,並引領市場。此外,根據 PlainID 2022 年存取和授權狀況報告,授權和身分驗證在 IAM 活動中優先考慮。
- 軟體即服務 (SaaS) 模型最初使客戶可以更輕鬆地存取應用程式,但隨著應用程式數量的激增,複雜性也迅速增加。每個應用程式都有自己的身份儲存、唯一的登入 URL 和密碼要求。這種憑證的激增降低了生產力並讓用戶感到沮喪,因為他們很難記住、重設和管理跨應用程式頻繁變化的密碼和 URL。這是各個終端用戶產業採用 IAM保全服務所面臨的主要市場挑戰。
- 受新冠肺炎疫情影響,一些公司提供了遠端工作選項,並在虛擬私人網路(VPN)上投入了比平常多得多的資金。辦公室中常見的實體安全措施在遠距工作時就不那麼重要了。這意味著組織必須採取更多措施來解決基於軟體的安全措施,包括 IAM 服務。因此,COVID-19 以及疫情後的遠端和混合工作模式正在加速全球市場的成長。
IAM保全服務市場趨勢
資訊科技和通訊領域有望實現強勁成長
- 多樣化的IT和通訊系統高度依賴基礎設施、網路和資料庫,因此容易受到資料外洩和竊盜的影響。此外,支援醫療保健和 BFSI 應用的 IT 外包計劃數量不斷增加正在推動市場成長。此外,現代 IT 經理對統一外包解決方案的概念也很感興趣。原因是這些選項都是使用過時的內部部署IT基礎設施的零碎附加元件解決方案的氾濫。
- 隨著資料庫和伺服器紛紛遷移到雲端,雲端服務在IT產業的普及度日益提升。此外,雲端運算支出的增加預計將推動雲端基礎的IAM 解決方案市場的發展。由於IT行業從業人員數量的不斷增加,個人資訊資料庫通常在雲端基礎的儲存中進行管理。此舉是為了因應 IAM 的雲化。
- 許多電信企業都擁有跨國的龐大用戶群。用戶依賴電訊系統進行各種金融和機密交易。由於數位身分和存取管治演算法的高度複雜性,電訊業對 IAM 解決方案的需求日益成長。
- 除此之外,IT 組織在安全方面的支出不斷增加預計將推動雲端基礎的IAM 的採用。知名通訊業者也開始轉型為技術供應商,透過創建用於網際網路通訊協定語音(VoIP)呼叫的行動應用程式並在雲端平台上儲存資料。此外,IT部門在安全方面的支出增加,加上行動性和雲端處理,預計將為營運商帶來新的風險,從而推動採用高度安全和強大的雲端發現平台。
- 例如,2022 年 12 月,著名的 IAM 供應商 Wallix 與超可信任雲端 3DS Outscale 合作,以加強其網路安全產品。 Wallix 的身份管理、身份驗證和數位存取安全解決方案目前在 Outscale 的市場上提供。 Wallix 和 3DS Outscale 幫助建立保護數位自由的可信任數位空間。 Outscale Marketplace 中資料的資料現在都受到設計保護,使用者可以決定是否共用他們的資料。因此,面臨在雲端中儲存敏感資料的挑戰的公共和私人組織可以透過滿足最高效能、安全性和資料保護要求的解決方案重新獲得對數位存取的控制,同時降低內部和外部網路風險。
北美以最大市佔率領先市場
- 北美地區有兩個新興經濟體-美國和加拿大,其IT服務業已經成熟。這些公司優先考慮許多 IAM 系統來保護登入憑證,並在單一、擴充性、多租戶解決方案中對其和其客戶的應用程式、網路和基礎設施實施最小特權存取。例如,多因素身份驗證、單一登入、特權存取管理、技術人員的提升存取權限、機密管理、整合目錄服務等。
- 例如,2022年6月,美國IAM平台供應商Evo Security推出了Evo Partner Identity Cloud。 Identity Cloud 是第一個專為滿足託管服務提供者 (MSP) 及其商業客戶的需求而設計的一體化 IAM 解決方案。這個企業級雲端平台是一個全面的識別及存取管理解決方案,它為 MSP 提供了一種簡單、高度安全的方式來保護中小型企業和大型企業免受利用登入和存取漏洞滲透網路和雲端資產的最常見類型的網路安全攻擊。
- 由於缺乏門禁系統,該地區的許多金融機構都遭遇了安全漏洞。這是因為銀行、金融服務和保險 (BFSI) 行業持有寶貴的資料,而且隨著邁向數位化時代,其潛力正在增加。例如,2022年4月,美國行動付款公司Block Inc.的一名未經授權的員工未經許可下載了一份客戶資訊報告。該調查估計涉及 820 萬現有和以前的消費者。
- 小型企業是加拿大經濟的支柱。隨著小型企業適應數位經濟和 COVID-19 疫情的持久影響,加拿大政府將幫助它們繼續成長、繁榮並創造良好的就業機會。加拿大政府打算啟動一項新的數位基礎設施計劃,以改善該國的供應鏈,使製造業和零售商受益。 2022 年 10 月,交通部長承諾投資 1.36 億加元,推動加拿大供應鏈產業主導的數位化。該國小規模工業的數位化趨勢可能會推動對 IAM 解決方案的需求,因為 IAM 解決方案將使企業能夠確保其數位化業務所需的安全性。
- 此外,2022年3月,加拿大總理宣布成立加拿大數位化採用計畫(CDAP),該計畫將幫助加拿大小型企業增加其線上影響力並更新或採用數位技術。該投資將在四年內提供 40 億美元,以支持多達 16 萬家中小型企業。 CDAP 將使加拿大小型企業能夠評估其數位化準備程度並在線上提交津貼貸款申請。中小企業可以利用這筆資金來實現數位技術的現代化和應用、業務流程數位化以及利用電子商務來保持競爭力。因此,該國中小企業的成長速度和數位技術的採用可能會為 IAM 服務提供者創造機會並刺激該地區的市場成長。
IAM保全服務產業概覽
IAM保全服務市場較為分散。大多數市場參與者正在考慮採取措施,透過專注於產品多樣化和開發來增加市場佔有率並佔領更大的市場佔有率。
2023 年 1 月,商業身分安全公司 SailPoint Technologies Inc. 收購了第三方身分風險解決方案供應商 SecZetta。收購 SecZetta 將使 SailPoint 能夠擴展其功能,幫助公司從單一的、市場領先的身份安全平台更好地了解所有類型的身份,包括員工和非員工身份,從第三方承包商到臨時工。此次收購為公司提供了所需的集中化方法,以及在整個企業內全面檢驗非員工身份所需的適當身份驗證。
此外,2022 年 11 月,全球獨立科技公司 Positive Thinking Company 與 Okta 合作,協助企業實現對目標系統的安全存取。 Okta 因其產品能夠涵蓋所有 IAM使用案例、易於使用、能夠靈活地與各種應用程式整合以及提供高品質的文件而脫穎而出。這些優勢與 Positive Thinking Company 的整合經驗相結合,將使兩家公司能夠與共同客戶建立長期關係,為他們提供滿足所有身分需求的一站式服務。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 調查結果
- 調查前提
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場動態
- 市場概況
- 市場促進因素與限制因素簡介
- 市場促進因素
- 安全擔憂日益加劇
- 網路資料外洩事件不斷增加
- 市場限制
- 安全解決方案成本高昂
- 與現有網路整合的複雜性
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 購買者/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭強度
第5章 市場區隔
- 按解決方案類型
- 身分雲
- 身分管治
- 存取管理
- 目錄服務
- 其他解決方案
- 依部署類型
- 本地
- 混合
- 雲端基礎
- 按組織規模
- 大型企業
- 中小企業
- 按行業
- BFSI
- 資訊科技/通訊
- 教育
- 衛生保健
- 零售
- 能源
- 製造業
- 其他最終用戶產業
- 地區
- 北美洲
- 美國
- 加拿大
- 歐洲
- 英國
- 德國
- 法國
- 其他歐洲國家
- 亞太地區
- 中國
- 日本
- 印度
- 其他亞太地區
- 拉丁美洲
- 巴西
- 墨西哥
- 其他拉丁美洲國家
- 中東和非洲
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 其他中東和非洲地區
- 北美洲
第6章 競爭格局
- 公司簡介
- IBM Corporation
- Oracle Corporation
- Broadcom Inc.
- Microsoft Corporation
- Amazon Web Services
- Centrify Corporation
- Okta Inc.
- Cyberark Software Ltd.
- Sailpoint Technologies, Inc.
- HID Global Corporation
- NetIQ Corporation
第7章投資分析
第8章 市場機會與未來趨勢
The IAM Security Services Market size is estimated at USD 19.15 billion in 2025, and is expected to reach USD 34.22 billion by 2030, at a CAGR of 12.31% during the forecast period (2025-2030).

Key Highlights
- Identity and access management (IAM) enables the right people, software, and hardware, as appropriate to job roles and functionality, to have access to the tools required to perform assigned duties without also granting them access to those that are not needed and/or present a security risk to the enterprise. Organizations that utilize IAM can streamline operations by managing identities without requiring individuals to log into applications as administrators.
- Cloud technology is changing how businesses work, driven by cost efficiencies and economies of scale. However, the lack of effective security can undermine the benefits of cloud computing. This marks the fundamental need for security solutions, including security for identity-related crime, driving the IAM market.
- IT operating costs of any organization can be reduced through IAM services because, with IAM services, companies no longer require local IDs for external usage, simplifying application administration. Cloud-based IAM services can decrease the requirement to purchase and maintain on-premises infrastructure, further fuelling market adoption.
- IAM software enables businesses to have entire administration regarding identities and access to internal networks. Businesses can implement reliable password rules and two-step verification. These enable multi-factor authentication (MFA), which keeps enterprises' security up to date and allows the companies to carry out their security strategy, driving the market. In addition, according to the PlainID 2022 State of Access and Authorization report, authorization and authentication have been prioritized in IAM activities.
- The software-as-a-service (SaaS) model initially makes it simpler for customers to access their applications, but complexity quickly rises as more applications are added. Each application has its identity store, unique login URLs, and password requirements. As users struggle to remember, reset, and manage these frequently changing passwords and URLs across their applications, this proliferation of credentials reduces user productivity and increases user annoyance. This is a major market challenge in implementing IAM security services in various end-user industries.
- Due to COVID-19, several businesses offered remote work options and invested significantly more than usual in a virtual private network (VPN. Physical security procedures are common in an office setting, although they are less crucial when working remotely. This means organizations must work more on software-based safeguards, including IAM services. Thus, COVID-19 and the post-pandemic scenario of remote and hybrid working models have accelerated market growth worldwide.
IAM Security Services Market Trends
The IT & Telecom Segment is Expected to Register a Strong Growth
- The diverse ecosystem of IT and telecommunication is more prone to data breaches and theft as they are highly dependent on their infrastructure, network, and databases to carry out any operation. Furthermore, the growing number of IT outsourced projects supporting applications in healthcare and BFSI has been driving the market growth. Moreover, modern IT administrators are attracted to the concept of a unified, outsourced solution because the alternative is a mess of partial add-on solutions with outdated on-premise IT infrastructure.
- The IT industry's penetration of cloud services is rising daily as databases and servers are now being shifted to the cloud. Also, growth in cloud spending is expected to drive the cloud-based IAM solution market. The growth in the number of employees in the IT industry has led to the database of personal details being usually maintained over cloud-based storage. This move is in anticipation of the shifting IAM in the cloud.
- Telecom businesses mostly work with a vast user base across national boundaries. The users consider that the telecom system can be relied upon for various transactions that could be financial or sensitive. Within the telecom industry, digital identities and access governance algorithms are very complex, thus driving the demand for IAM solutions.
- In addition to this, growth in security spending in IT organizations is expected to drive cloud-based IAM adoption. Prominent telecom organizations have also begun to transform themselves into technology providers by creating mobile applications for the use of voice over internet protocol (VoIP) calls and storing data on cloud platforms. In addition, growth in security spending in IT organizations, along with the combined mobility and cloud computing, is expected to create new frontiers of risks for operators, thereby driving the adoption of a highly secure and robust cloud discovery platform.
- For instance, in December 2022, Wallix, a prominent IAM provider, joined forces with hyper-trust cloud 3DS Outscale to strengthen its cybersecurity offering. Wallix's identity management, authentication, and digital access security solutions are now available on the Outscale marketplace. Wallix and 3DS Outscale will help build a trusted digital space that preserves digital freedom. Personal and industrial data stored in the Outscale marketplace is now protected by design, meaning users can decide whether to share their data. As a result, public and private organizations that face the challenge of storing sensitive data on the cloud can regain control of digital access by utilizing a solution that meets the highest performance, security, and data protection requirements, while reducing internal and external cyber risk.
North America Leads the Market with the Largest Market Share
- The North American region has two developed economies, including the United States and Canada, with well-established IT service sectors. These businesses have prioritized many IAM systems to protect login credentials and apply for least-privilege access across applications, networks, and infrastructure for themselves and their clients in a single scalable, multi-tenant solution. Examples include multi-factor authentication, single sign-on, privileged access management, technician elevated access, secrets management, and unified directory services.
- For instance, in June 2022, Evo Security, an American IAM platform provider, launched the Evo Partner Identity Cloud. This identity cloud is the first all-in-one IAM solution designed exclusively with the needs of managed service providers (MSPs) and their business customers in mind. The enterprise-grade cloud platform is a comprehensive identity and access management solution that gives MSPs an easy and highly secure way to protect small and medium-sized businesses and enterprises from the most common types of cybersecurity attacks that frequently exploit login and access vulnerabilities to penetrate network and cloud assets.
- Many financial institutions in the region have been witnessing security breaches due to a lack of access management systems. This is because the banking, financial services, and insurance (BFSI) sector holds valuable data, and their efforts to transition to the digital age are raising the possibility. For instance, in April 2022, unauthorized employees of the US mobile payment company, Block Inc., downloaded client information reports without permission. It is estimated that 8.2 million current and former consumers were included in the research.
- Small businesses are the backbone of the Canadian economy. As small businesses adapt to the digital economy and the lasting impacts of the COVID-19 pandemic, the Government of Canada is working to help them continue to grow, thrive, and create good jobs. The Canadian government intends to start a new digital infrastructure project to improve the country's supply chains which would be helpful country's manufacturing and Retail industries' vendors. In October 2022, the Minister of Transport declared to invest USD 136 million initiative in Advancing Industry-Driven Digitalization of Canada's Supply Chain. This digitalization trend among the small industries in the country would drive the requirement for IAM solutions because IAM solutions enable companies to have the desired security for their digital operations.
- Additionally, in March 2022, the prime minister of Canada announced the establishment of the Canada Digital Adoption Program (CDAP), which would help Canadian small and medium-sized businesses increase their online presence and update or implement digital technologies. This investment would provide USD 4 billion over four years to support up to 160,000 small businesses. The CDAP would enable small and medium-sized enterprises in Canada to assess their level of digital readiness and submit grant and loan applications online. They could utilize this cash to modernize or embrace digital technologies, digitize their business processes, and take advantage of e-commerce opportunities to stay competitive. Thus, the increasing rate of SMBs in the country and their adoption of digital technology would create an opportunity for the IAM service providers and fuel the market growth in the region.
IAM Security Services Industry Overview
The IAM security services market is fragmented. The vast majority of the players in the market are considering steps to raise their market footprint by focusing on product diversification and development, making them grab a larger market share.
In January 2023, SailPoint Technologies Inc, a company in business identity security, acquired SecZetta, a third-party identity risk solutions provider. With SecZetta, SailPoint will be able to expand its capabilities to help companies gain better visibility into all types of identities, across both employee and non-employee identities - from third-party contractors to temporary workers - all from a single, market-leading identity security platform. This acquisition will give enterprises the centralized approach needed, plus the proper identity proofing required to validate non-employee identities across their businesses fully.
Moreover, in November 2022, Positive Thinking Company, a global independent technology company, partnered with Okta to help companies enable secure access to their target systems. Okta stands out with its product capabilities covering all IAM use cases, products' ease of use, flexibility in integrating with a broad number of apps, and the high quality of documentation available. Combining those strengths with Positive Thinking Company's integration experience, they will nurture long-term relationships with their joint customers, providing them with a one-stop shop for all their identity needs.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Study Assumptions
- 1.3 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Increasing Security Concerns
- 4.3.2 Increasing Number of Cyber Data Breaches
- 4.4 Market Restraints
- 4.4.1 High Costs of Security Solution
- 4.4.2 Complexity in Integration with Existing Network
- 4.5 Industry Attractiveness - Porter's Five Forces Analysis
- 4.5.1 Threat of New Entrants
- 4.5.2 Bargaining Power of Buyers/Consumers
- 4.5.3 Bargaining Power of Suppliers
- 4.5.4 Threat of Substitute Products
- 4.5.5 Intensity of Competitive Rivalry
5 MARKET SEGMENTATION
- 5.1 By Type of Solutions
- 5.1.1 Identity Cloud
- 5.1.2 Identity Governance
- 5.1.3 Access Management
- 5.1.4 Directory Services
- 5.1.5 Other Type of Solutions
- 5.2 By Type of Deployment
- 5.2.1 On-premise
- 5.2.2 Hybrid
- 5.2.3 Cloud-based
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small & Medium Enterprises (SMEs)
- 5.4 By End-user Vertical
- 5.4.1 BFSI
- 5.4.2 IT & Telecom
- 5.4.3 Education
- 5.4.4 Healthcare
- 5.4.5 Retail
- 5.4.6 Energy
- 5.4.7 Manufacturing
- 5.4.8 Other End-user Vertical
- 5.5 Geography
- 5.5.1 North America
- 5.5.1.1 US
- 5.5.1.2 Canada
- 5.5.2 Europe
- 5.5.2.1 UK
- 5.5.2.2 Germany
- 5.5.2.3 France
- 5.5.2.4 Rest of Europe
- 5.5.3 Asia Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 Rest of Asia-Pacific
- 5.5.4 Latin America
- 5.5.4.1 Brazil
- 5.5.4.2 Mexico
- 5.5.4.3 Rest of Latin America
- 5.5.5 Middle East and Africa
- 5.5.5.1 Saudi Arabia
- 5.5.5.2 UAE
- 5.5.5.3 Rest of Middle East and Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 IBM Corporation
- 6.1.2 Oracle Corporation
- 6.1.3 Broadcom Inc.
- 6.1.4 Microsoft Corporation
- 6.1.5 Amazon Web Services
- 6.1.6 Centrify Corporation
- 6.1.7 Okta Inc.
- 6.1.8 Cyberark Software Ltd.
- 6.1.9 Sailpoint Technologies, Inc.
- 6.1.10 HID Global Corporation
- 6.1.11 NetIQ Corporation










