 |
市場調查報告書
商品編碼
1637786
中東和非洲的網路安全 -市場佔有率分析、行業趨勢/統計、成長預測(2025-2030)MEA Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
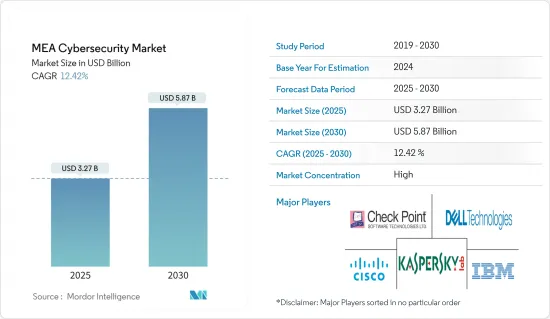
中東和非洲網路安全市場規模預計到 2025 年為 32.7 億美元,預計到 2030 年將達到 58.7 億美元,預測期內(2025-2030 年)複合年成長率為 12.42%。
主要亮點
- 在當前的市場情況下,網路安全叢集可以透過地方政府的故意、通常自上而下的行動來成長,政府法規和政策對其市場發展至關重要。許多私人公司正在將業務轉移到雲端平台。
- 以石油為基礎的沙烏地阿拉伯擁有沿岸地區最大的經濟體,並致力於成為最重要的 IT 市場。多項政府措施以及國家轉型計畫 (NTP) 正在支持該地區 IT 的快速發展。沙烏地阿拉伯擁有油田,並佔據地緣政治高度緊張的地區,使其成為網路犯罪分子的熱門目標。根據 NTP舉措,政府預算申請40 億沙烏地里亞爾。主要關注領域是網路安全、智慧電網和控制關鍵基礎設施的地理空間 IT 系統。這種政府支持為IT安全公司在該國發揮積極作用奠定了基礎。
- 根據 Help AG 去年發布的市場狀況報告,光是阿拉伯聯合大公國的攻擊就增加了 183%。該國所有部門都多次遭受攻擊,包括政府、石油、衛生和電信。分散式阻斷服務 (DDoS) 規模持續成長,阿拉伯聯合大公國記錄達 254.3Gbps。此外,該國越來越多的中小企業和網路安全供應商專注於提供創新解決方案。因此,供應商預計將推出新產品作為其競爭策略的一部分。例如,總部位於阿拉伯聯合大公國的座標公司宣佈為中小型企業提供自適應客製化網路安全。
- 支持卡達應對當前和新出現的威脅和風險的努力,並支持卡達國家資訊通訊技術計劃,為各部門提供安全可靠的線上環境,並根據戰略主旨保護國家關鍵資訊基礎設施。 )由國家網路安全委員會(NCSC)制定。 NCSC 是根據總理決定 (18) 成立的,主要目的是為政府最高層的網路安全合作提供管治結構。
- 中東和非洲的網路安全人力資源數量較少。儘管如此,鑑於該地區的商業活動水平很高,它仍然是最容易受到網路攻擊的地區之一。此外,該地區的許多專業人士需要獲得更多經驗來應對日益嚴重的網路威脅。例如,Fircroft 表示,中東地區約有 30% 的網路安全工作者擁有 10 年以上的產業經驗。相比之下,60%的專業人士擁有5年以上的經驗。
- 在新冠肺炎 (COVID-19) 期間採用遠距工作的公司遭受的攻擊數量增加。據 IBM 稱,遠距工作是違規因素的違規行為的平均成本比遠距工作不是因素的違規行為高出 105 萬美元。根據 Proofpoint 2021 年進行的一項調查(受訪者:擁有 200 名或以上員工的組織的首席資訊安全安全官(CISO),N=1,400 人),阿拉伯聯合大公國約76% 的CISO、約69% 的CISO 表示遭受有針對性的攻擊自 2021 年遠距工作在全球廣泛普及以來,這種情況有所增加。
中東和非洲網路安全市場趨勢
雲端領域預計將高速成長。
- 雲端基礎的資安管理服務的日益使用正在簡化中東企業網路安全措施的實施。雲端安全是指保護雲端資料、應用程式和基礎架構免受威脅的技術、策略、控制和服務。作為現代化的網路安全解決方案,雲端安全不同於傳統安全。 IT 模型包括擴展速度、資料儲存、最終用戶系統介面以及與其他網路資料和系統的接近性等內容。
- 雲端運算改變了企業使用、共用和儲存資料、應用程式和工作負載的方式。然而,雲端運算也帶來了新的安全威脅和挑戰。隨著大量資料流入雲端和公共雲端服務,風險也在增加。阿拉伯聯合大公國的雲端市場仍處於起步階段,私有 LaaS 的引進被認為是邁向更廣泛的雲端採用的重要的第一步。如果在該地區開設雲端資料中心,預計雲端的採用將會加速,對雲端安全的需求也會增加。此外,該地區國家正在走向雲端運算的未來,這也將推動對雲端安全的需求。
- 中東和非洲的供應商需要利用雲端基礎的解決方案進行創新,以抓住市場機會。我們還希望建立全球資料中心以提高雲端彈性、滿足資料隱私法規並與公共雲端(AWS、Azure)整合以提高可擴展性。例如,巴林經濟發展委員會(EDB)與中國跨國高科技公司的雲端運算子公司騰訊雲端簽署了合作備忘錄(MoU),以促進巴林王國IDC的發展並建立網際網路資料中心(IDC),支持其迅速崛起為中東和北非地區雲端和IDC 領域的中心。此類公共雲端基礎設施的建立預計將推動中東和北非地區對雲端基礎的解決方案的需求。
- 然而,與中東地區相比,非洲在雲端解決方案的部署方面仍需迎頭趕上。盜版仍然是一個主要障礙,因為許多公司正在使用盜版軟體的舊版本地版本。然而,這使得企業面臨多種威脅。隨著全部區域安全威脅的頻率和複雜性不斷增加,該地區的供應商正在提供雲端 UTM,為組織提供全天候保護和雲端可擴展性。雲端 UTM 消除了本地防火牆管理的複雜性,並提供卓越的識別和威脅管理。例如,最近,阿拉伯聯合大公國綜合電信公司 (EITC) 推出了雲端統一威脅管理 (UTM) 服務,這是一種網路安全解決方案,可將組織的邊界安全地擴展到所有站點。
- 據 Turbonomic 稱,56% 的受訪者表示,他們將在 2021 年使用 Microsoft Azure 進行雲端服務。亞馬遜網路服務(AWS)在 2020 年之前一直位居榜首,但被微軟超越。此外,不使用任何雲端的受訪者比例從 2021 年的 4% 增加到去年的 8%。
BFSI可望引領市場
- 中東和非洲正在更廣泛的經濟發展背景下以及銀行業內部經歷數位轉型。在 COVID-19 之前,該地區的 BFSI數位化率較低,但隨著 COVID-19 的威脅和不確定性消退,金融服務業開始快速採用數位化以保持競爭力,以滿足不斷成長的客戶期望。利用雲端和人工智慧(AI) 等技術。
- 阿拉伯聯合大公國銀行業聯合會 (UBF) 將於 2021 年加入 49 家銀行的行列,宣布啟動一項新舉措,以應對未來所有網路威脅。作為該舉措的一部分,所有成員銀行將被要求無縫收集、分析和共用網路威脅的資料,從而實現匿名報告和警報管理。該舉措為金融機構提供了對當前網路威脅情勢的全面了解。這使得金融機構能夠更好地準備和應對任何威脅。
- 富查伊拉國家銀行 (NBF) 制定了穩健的網路安全策略,重點是三大支柱:身分驗證保護、資料保護和文化。此外,作為該銀行網路彈性計畫的一部分,它還進行了各種類型的網路攻擊模擬,包括紅隊演習、桌面網路攻擊模擬和網路釣魚模擬,以在專家的幫助下開發其網路彈性能力。
- 據AFDB稱,ACRC計劃有潛力使全部區域超過2.5億弱勢客戶和2,000多家金融機構受益。此外,作為其性別計劃的一部分,ACRC 將專門致力於在五年內改善 2,000 至 2,500 萬名女性的網路安全,並致力於僱用至少 39% 的女性。預計該地區 BFSI 部門對提高網路犯罪意識的投資將推動預測期內交付的解決方案的發展。
- 據米爾肯研究所稱,到 2022 年,中東地區金融科技 (fintech) 公司的數量預計將增加到 465 家。 2017年,該地區僅有30家金融科技公司。該地區金融科技公司的緩慢成長為本地和國際參與企業創造了開發新解決方案以獲得市場佔有率的機會。
中東和非洲網路安全產業概況
中東和非洲網路安全市場競爭激烈,由多家大公司組成。從市場佔有率來看,目前該市場由幾家大型企業主導。這些擁有顯著市場佔有率的領先公司致力於在全球擴大基本客群。這些公司利用策略合作計劃來增加市場佔有率和盈利。
2023年3月,國際民航組織與阿拉伯聯合大公國政府宣布了航空網路安全和創新領域的新進展和進展。國際民航組織和阿拉伯聯合大公國之間的夥伴關係預計將加強網路安全、加速器和民用航空未來創新的知識共用和經驗。
其他好處
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場動態
- 市場概況
- 市場促進因素
- 網路安全事件快速增加
- 來自地下市場的持續威脅
- 市場限制因素
- 網路安全專家短缺
- 高度依賴傳統認證方式且準備不足
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 買家/消費者的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭公司之間的敵對關係
- 技術簡介
- 安全類型
- 網路
- 雲
- 應用
- 終點
- 無線網路
- 其他安全類型
- 產業價值鏈分析
- COVID-19 市場影響評估
- 安全類型
第5章市場區隔
- 解決方案
- 威脅情報和回應管理
- 身份驗證和存取管理
- 預防資料外泄管理
- 安全和漏洞管理
- 統一威脅管理
- 企業風險與合規
- 服務
- 託管服務
- 專業服務
- 部署
- 雲
- 本地
- 最終用戶
- 航太/國防
- BFSI
- 醫療保健
- 製造業
- 零售
- 政府機構
- 資訊科技/通訊
- 其他
- 國家名稱
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 南非
- 其他中東/非洲
第6章 競爭狀況
- 公司簡介
- Cisco Systems Inc.
- Dell Technologies
- Kaspersky Lab
- IBM Corporation
- Check Point Software Technologies Ltd
- Palo Alto Networks Inc.
- Broadcom Inc.(Symantec Corporation)
- Trend Micro Inc.
- FireEye Inc.
- Paramount Computer Systems LLC
- DTS Solutions Inc
第7章 投資分析
第8章市場的未來
The MEA Cybersecurity Market size is estimated at USD 3.27 billion in 2025, and is expected to reach USD 5.87 billion by 2030, at a CAGR of 12.42% during the forecast period (2025-2030).

Key Highlights
- In the current market scenario, Cybersecurity clusters can grow organically or develop through intentional, often top-down actions taken by local governments, and government regulations and policies play a significant role in their development. Many private firms have been moving their operations to the cloud platform.
- Saudi Arabia, an oil-based economy, is the largest in the Gulf region and aims to be the most prominent IT market. Like the National Transformation Program (NTP), several government initiatives have supported the region's rapid IT development. Saudi Arabia is a popular target for cybercriminals due to its oil wells and occupancy of an area prevalent with geopolitical tensions. Under the NTP initiative, the government outlined SAR 4 billion for ICT development from 2016 until the previous year. The main focus areas are cybersecurity, smart grid, and geospatial IT systems to control significant infrastructure. Such a push from the government provides scope for IT security companies to flourish within the country.
- According to Help AG's State of the Market Report of the previous year, there was a 183% rise in attacks in the UAE alone. All sectors in the nation faced repeated attacks, including the government, oil, healthcare, and telecom. Distributed Denial of Service (ddos) has only increased in scale, according to the company, with the UAE measuring 254.3 Gbps. Further, the growth in the number of smes and cybersecurity vendors in the country is directing focus on offering innovative solutions. Thus, vendors are expected to adopt new launches as part of their competitive strategy. For example, UAE-based Coordinates announced Adaptive Bespoke Cybersecurity for SME.
- To support Qatar's efforts to address the current and emerging threats and risks, and in light of the strategic thrusts of Qatar's National ICT Plan to protect the national critical information infrastructure providing a safe and secure online environment for the different sectors, Qatar National Cyber Security Strategy (NCSS) was created by the National Cyber Security Committee (NCSC). The NCSC was primarily established under the Prime Minister's Decision No. (18) to provide a governance structure for collaboratively addressing cyber security at the highest levels of the government.
- The Middle East & Africa region have smaller numbers of cybersecurity workforces. Still, considering the region's high degree of business activities, it is one of the most attractive regions for cyber attacks. Also, most professionals in this region need to be more experienced in dealing with the intensity of incoming cyber threats. For instance, According to Fircroft, around 30% of all cybersecurity workforce in the Middle East have just over ten years of experience working in the industry. In comparison, 60% of these professionals have more than five years of experience.
- Enterprises adopting remote working during the covid-19 increased the number of attacks. According to IBM, the average cost was USD 1.05 million higher in breaches where remote work was a factor in causing the breach compared to those where remote work was not a factor. According to a study by Proofpoint in 2021 (N=1,400 respondents; Chief Information Security Officers (cisos) from organizations with more than 200 employees), about 76% CISO's from UAE and 69% of CISO's from KSA part of the study mentioned their business had seen more targeted attacks since enabling widespread remote working worldwide in 2021.
Middle East & Africa Cybersecurity Market Trends
Cloud Segment is expected to grow at a higher pace.
- The increasing use of cloud-based managed security services has even simplified the adoption of cybersecurity practices for Middle Eastern enterprises. Cloud security refers to the technologies, policies, controls, and services that protect cloud data, applications, and infrastructure from threats. Cloud security stands out from the legacy as a modernized cyber security solution. IT models include scaling speeds, data storage, end-user system interfacing, and proximity to other networked data and systems.
- Cloud computing has transformed how enterprises use, share, and store data, applications, and workloads. However, it has also introduced a host of new security threats and challenges. Significant data going into the cloud and public cloud services increases the exposure. The cloud market in UAE is still in the early stages, with the implementation of private laaS viewed as a critical first step towards broader cloud adoption. The opening of cloud data centers in the region is likely to boost cloud adoption, which would drive the demand for cloud security. Also, initiatives by the countries in the region to move towards a cloud computing future are poised to propel the demand for cloud security.
- To tap the market opportunities, vendors in MEA need to innovate cloud-based solutions. They also want to build global data centers to strengthen cloud resilience, meet data privacy regulations, and engage with the public cloud (AWS, Azure) for higher scalability.For instance, Bahrain Economic Development Board (EDB) signed a Memorandum of Understanding (MoU) with Tencent Cloud, the cloud computing subsidiary of the multinational Chinese tech firm, to drive the Kingdom of Bahrain's IDC development and support its rapid emergence as the MENA region's hub for the cloud and IDC sectors by opening an Internet Data Centre (IDC) in the country. Establishing such public cloud infrastructures is expected to drive the demand for cloud-based solutions in the MENA region.
- However, Africa still needs to catch up to the deployment of cloud solutions as compared to the Middle Eastern region. Piracy is still a big hurdle as many businesses use legacy on-prem versions of pirated software. However, this exposes the company to multiple threats. With security threats across the region increasing in frequency and sophistication, vendors in the area are offering Cloud UTM that provides organizations with around-the-clock protection and the cloud's scalability. It eliminates the complexity of managing on-premise firewalls and delivers superior identification and threat management. For instance, recently, du, from Emirates Integrated Telecommunications Company (EITC), has launched its Cloud Unified Threat Management (UTM) service, a cybersecurity solution that extends organizations' perimeters to all sites securely.
- According to Turbonomic, in 2021, 56 % of respondents said they use Microsoft Azure for cloud services. Amazon Web Services (AWS) topped the ranking until 2020 when Microsoft surpassed it. Furthermore, the percentage of respondents who do not use any cloud increased from 4% in 2021 to 8% in the last year.
BFSI is Expected to Drive the Market
- The Middle Eastern and African region is undergoing digital transformations from a broader economic development context and within the banking sector. Before COVID-19, BFSI digitalization rates in the area were low; however, as the threat and uncertainty from COVID-19 settled in, the financial services industry is started adopting digitization at a rapid pace and utilizing technologies such as cloud, artificial intelligence (AI), to meet rising customer expectations to remain competitive.
- The UAE Banks Federation (UBF), a professional body representing 49 banks as members in 2021, announced that it is launching a new initiative to combat all future cyber threats. As a part of this initiative, all the member banks will have to seamlessly collect, analyze and share data on cyber threats while allowing anonymous reporting and alert management. The initiative will enable financial institutions to gain an encompassing perceptive of the ongoing cyber threat landscape. It will allow them to better prepare and respond to all emergent threats.
- The National Bank of Fujairah (NBF) has built a robust cybersecurity strategy focusing on three main pillars: identity protection, data protection, and culture. Moreover, as part of the bank's cyber resiliency program, it conducts various types of cyberattack simulations like the Red Team exercise, Tabletop Cyber Attack Simulations, and Phishing simulations, among others, to measure our cyber resiliency capabilities with the help of specialists.
- According to AFDB, this ACRC project has the potential to benefit over 250 million vulnerable clients and over 2,000 financial institutions across the region. Moreover, as part of its gender promotion policy, ACRC will specifically target improving cybersecurity for 20 to 25 million women in five years and will aim to employ a workforce of at least 39% of women. Investments in the awareness of cybercrime in the BFSI sector in the region are expected to drive the development of solutions offered during the forecasted period.
- According to Milken Institute, in the Middle East area, the number of financial technology (FinTech) enterprises is predicted to grow to 465 by 2022. There were just 30 fintech companies in the region in 2017. The gradual growth of fintech firms in the region creates an opportunity for the local and international players to develop new solutions to capture the market share.
Middle East & Africa Cybersecurity Industry Overview
The cybersecurity market in the Middle East and Africa is highly competitive and consists of several major players. In terms of market share, few of the major players currently dominate the market. These major players with a prominent market share are focusing on expanding their customer bases across foreign countries. These companies leverage strategic collaborative initiatives to increase their market shares and profitability.
In March 2023, the International Civil Aviation Organization announced new developments and progress in areas of aviation cybersecurity and innovation with the UAE Government. The ICAO-UAE partnership is expected to enhance knowledge sharing and experience in terms of cybersecurity, accelerators, and innovation in future civil aviation.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rapidly Increasing Cyber Security Incidents
- 4.2.2 Consistent Threats From the Underground Market
- 4.3 Market Restraints
- 4.3.1 Lack of Cyber Security Professionals
- 4.3.2 High Reliance on Traditional Authentication Methods and Low Preparedness
- 4.4 Industry Attractiveness - Porter's Five Force Analysis
- 4.4.1 Threat of New Entrants
- 4.4.2 Bargaining Power of Buyers/Consumers
- 4.4.3 Bargaining Power of Suppliers
- 4.4.4 Threat of Substitute Products
- 4.4.5 Intensity of Competitive Rivalry
- 4.5 Technology Snapshot
- 4.5.1 Security Type
- 4.5.1.1 Network
- 4.5.1.2 Cloud
- 4.5.1.3 Application
- 4.5.1.4 End-point
- 4.5.1.5 Wireless Network
- 4.5.1.6 Other Security Types
- 4.5.2 Industry Value Chain Analysis
- 4.5.3 Assessment of Impact of COVID-19 on the Market
- 4.5.1 Security Type
5 MARKET SEGMENTATION
- 5.1 Solution
- 5.1.1 Threat Intelligence and Response Management
- 5.1.2 Identity and Access Management
- 5.1.3 Data Loss Prevention Management
- 5.1.4 Security and Vulnerability Management
- 5.1.5 Unified Threat Management
- 5.1.6 Enterprise Risk and Compliance
- 5.2 Service
- 5.2.1 Managed Services
- 5.2.2 Professional Services
- 5.3 Deployment
- 5.3.1 Cloud
- 5.3.2 On-premise
- 5.4 End User
- 5.4.1 Aerospace and Defense
- 5.4.2 BFSI
- 5.4.3 Healthcare
- 5.4.4 Manufacturing
- 5.4.5 Retail
- 5.4.6 Government
- 5.4.7 IT and Telecommunication
- 5.4.8 Other End users
- 5.5 Country
- 5.5.1 Saudi Arabia
- 5.5.2 United Arab Emirates
- 5.5.3 South Africa
- 5.5.4 Rest of Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Cisco Systems Inc.
- 6.1.2 Dell Technologies
- 6.1.3 Kaspersky Lab
- 6.1.4 IBM Corporation
- 6.1.5 Check Point Software Technologies Ltd
- 6.1.6 Palo Alto Networks Inc.
- 6.1.7 Broadcom Inc. (Symantec Corporation)
- 6.1.8 Trend Micro Inc.
- 6.1.9 FireEye Inc.
- 6.1.10 Paramount Computer Systems LLC
- 6.1.11 DTS Solutions Inc













