 |
市場調查報告書
商品編碼
1644883
中國網路安全:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030 年)China Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
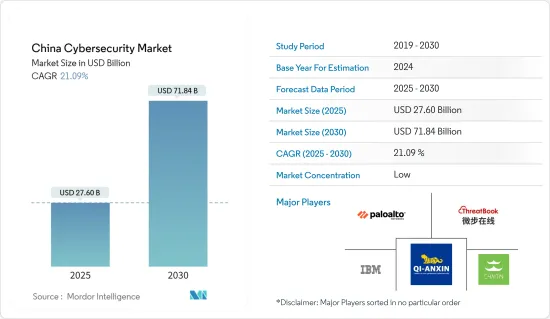
2025年中國網路安全市場規模預估為276億美元,預估至2030年將達718.4億美元,預測期間(2025-2030年)複合年成長率為21.09%。
隨著數位化進程的推進和網路威脅的增加,中國的網路安全市場正在快速成長。中國政府積極加強網路安全措施,保護關鍵基礎設施、敏感資料和企業免受網路攻擊。
主要亮點
- 中國的技術進步正在增加連網設備的數量。隨著 5G 設備的發展,設備互聯互通也呈指數級成長。因此,連網設備的數量將會增加,進而大幅增加安全產品的市場需求。
- 隨著物聯網的興起,工業革命 4.0 將有助於跨產業的蜂巢式連接。機器對機器的連結也正在推動市場的發展。根據CNNIC預測,到2023年12月,中國約有23.3億網路用戶可使用蜂巢式物聯網服務。智慧公共、製造業和運輸業佔物聯網終端用戶的一半以上。
- 網路攻擊增加的主要原因之一是各行業缺乏熟練的網路安全人才。在中國,與安全專業人員相比,經驗豐富的網路安全專家非常稀缺,他們被要求解決金融機構、政府機構和私人企業/產業的網路威脅。
- 大型企業正在為安全和銷售部署更多資料驅動的人工智慧解決方案。網路安全專家正在利用地理空間資料來加強他們的防線。透過將地理空間資料納入現有的安全系統,公司可以增強緊急管理、國家情報、基礎設施保護和防禦平台。
- 自新冠肺炎疫情以來,包括中國在內的許多國家組織已轉向遠距工作環境。包括惡意軟體和勒索軟體在內的網路攻擊的增加迫使組織採用網路安全解決方案。因此,隨著在家工作趨勢的日益成長,中國的網路安全市場預計將顯著成長。
中國網路安全市場趨勢
雲端部署領域預計將佔據重要市場佔有率
- 隨著企業越來越認知到將資料遷移到雲端而不是創建和維護新的資料儲存可以節省成本和資源,對雲端基礎的解決方案的需求以及隨之而來的按需安全服務的使用成長也隨之而來。由於這些優勢,雲端基礎的解決方案正被中國大大小小的企業頻繁採用。
- 企業越來越意識到將資料遷移到雲端而不是建置和維護新的資料儲存對於節省成本和資源的重要性,這推動了對雲端基礎的解決方案的需求。鑑於其多種優勢,雲端平台和生態系統有望成為未來幾年爆發數位創新速度和規模的發射台。
- 隨著 IT 交付從內部部署轉向外部部署,安全性在雲端引進週期的每個階段都變得至關重要。中小型企業更願意採用雲端運算,因為它允許他們將有限的網路安全資金集中在核心競爭力上,而不是投資於安全基礎設施。此外,隨著公有雲端服務的使用擴大了組織的信任邊界,安全性成為雲端基礎設施的重要組成部分。然而,雲端基礎方案的廣泛使用大大簡化了企業的網路安全工作。
- Google Drive、Dropbox 和 Microsoft Azure 等雲端服務的日益普及,以及這些工具成為業務流程不可或缺的一部分的出現,迫使企業解決敏感資料失控等安全性問題。這就是為什麼按需網路安全解決方案的採用日益增多的原因。
- 雲端基礎的解決方案還具有降低資本支出要求的好處,使商業案例更加強大。透過採用雲端基礎的服務,企業可以大幅減少資本支出需求,因為他們不需要投資硬體元件。雲端解決方案還可以使應用程式成本更加可預測,因此公司不必花費太多的前期成本來部署該技術。硬體和 IT 支援方面的節省使得雲端基礎的解決方案更加經濟實惠。
- 考慮從內部部署軟體遷移到雲端基礎的解決方案的公司主要會檢查潛在解決方案在關鍵安全功能(例如標準合規性、入侵防禦和檢測)方面的功能。
- CNNIC於2023年6月進行的一項調查發現,20%的中國網路使用者曾成為網路詐騙的受害者。
資料安全產品領域預計將佔據相當大的市場佔有率
- 金融業被公認為採用監管框架並建立適當資訊和資料安全標準的領先產業。這確保了貨物和服務的可靠交付、我們的系統安全處理資料以及負責任地使用您的個人資料。
- 資料安全降低了保護敏感資料免受威脅所帶來的風險,並幫助組織保持合規性。資料安全平台提供資料風險分析、資料監控、保護解決方案,保護組織資料免受資料庫漏洞的影響。各國政府正在加強資料安全監管,並要求企業使用網路安全解決方案。這一趨勢包括使用防毒和反間諜軟體,預計將在未來幾年內創造一個蓬勃發展的網路解決方案市場。合規性有望成為預防資料外泄解決方案的主要驅動力。然而,企業的數位轉型策略,特別是雲端運算採用、巨量資料分析和物聯網支持,也在推動該地區的企業安全團隊採用這些產品,在整個組織內識別和分類關鍵資料,並主要根據資訊的關鍵性重新分配資料安全控制。
- 隨著企業不斷實現業務數位化並應對日益複雜的資料保護挑戰,投資有效的資料安全措施對於保護敏感資訊、維持法規合規性和保護企業聲譽至關重要。
- 隨著數位轉型的加速和資料保護問題變得更加複雜,組織必須投資正確的安全措施來保護敏感資料,滿足監管要求並保護其品牌形象。由於資料量的增加、資料保護條例的變化以及客戶相關擔憂,對資料安全解決方案的需求預計會增加。
- 根據CNNIC 2023年6月的調查顯示,網路詐騙是中國網友面臨的最常見的網路安全問題。約有 38% 的受訪者曾遭遇網路抽獎或樂透中獎詐騙。
中國網路安全產業概況
中國的網路安全市場較為分散,領先的公司包括Palo Alto Networks、ThreatBook、IBM Corporation、奇安信科技Group Limited和北京長亭未來科技等。市場參與者正在採取合作和收購等策略來增強其產品供應並獲得永續的競爭優勢。例如
- 2024 年 4 月,全球網路安全領導者 Palo Alto Networks 和 Google Cloud 宣布擴大夥伴關係,並承諾提供十位數的多年期資金。 Palo Alto Networks 選擇 Google Cloud 作為其 AI 和基礎設施供應商。 Google Cloud 早已將 Palo Alto Networks 視為其首選的新一代防火牆 (NGFW) 供應商,而此次擴展的協議鞏固了這種關係。此次合作也凸顯了人工智慧平台自動化和整合多種解決方案以提供近乎即時的安全解決方案的關鍵重要性。
- 2023 年 10 月,IBM 宣布其託管檢測和響應服務的改進,利用 AI 技術自動升級或關閉高達 85% 的警報,縮短客戶的安全響應時間。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3 個月的分析師支持
目錄
第 1 章 簡介
- 研究假設和市場定義
- 研究範圍
第2章調查方法
第3章執行摘要
第4章 市場洞察
- 市場概況
- 產業價值鏈分析
- 產業吸引力-波特五力分析
- 供應商的議價能力
- 購買者/消費者的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭對手之間的競爭強度
- 宏觀經濟因素如何影響市場
第5章 市場動態
- 市場促進因素
- 企業面臨的網路釣魚和惡意軟體風險日益增加
- 增加雲端基礎的服務的使用
- 日益成長的 M2M/IoT 連線要求企業加強網路安全
- 市場限制
- 網路安全專家短缺和最新設備的安全挑戰
- 組織面臨預算限制、準備不足以及對傳統身分驗證方法的高度依賴
- 市場機會
- 物聯網、BYOD、人工智慧和機器學習在網路安全領域的發展趨勢
- 改變傳統防毒軟體產業
第6章 市場細分
- 按服務
- 安全類型
- 雲端安全
- 資料安全
- 身分和存取管理
- 網路安全
- 消費者安全
- 基礎設施保護
- 其他類型
- 按服務
- 安全類型
- 按部署
- 雲
- 本地
- 按最終用戶
- BFSI
- 衛生保健
- 製造業
- 政府和國防
- 資訊科技/通訊
- 其他最終用戶
第7章 競爭格局
- 公司簡介
- Palo Alto Networks
- ThreatBook
- IBM Corporation
- QI-ANXIN Technology Group Inc.
- Beijing Chaitin Future Technology Co. Ltd
- CoreShield Times
- River Security
- Tophant Inc.
- iJiami
- IDsManager
第8章投資分析
第9章:未來市場展望
The China Cybersecurity Market size is estimated at USD 27.60 billion in 2025, and is expected to reach USD 71.84 billion by 2030, at a CAGR of 21.09% during the forecast period (2025-2030).

China's cybersecurity market has been rapidly growing with the country's increasing digitization and the corresponding rise in cyber threats. The Chinese government has been actively enhancing its cybersecurity measures to protect critical infrastructure, sensitive data, and businesses against cyber attacks.
Key Highlights
- The number of connected devices has increased in China due to technological advancements. The interconnectivity of the devices also grows exponentially with 5G-enabled devices. As a result, there are more connected devices, which immediately increases the market's need for security products.
- Industrial Revolution 4.0 aids cellular connectivity throughout the industry with the rise of IoT. Machine-to-machine connections have also been instrumental in driving the market. According to CNNIC, in December 2023, approximately 2.33 billion internet users in China had access to cellular Internet of Things (IoT) services. Smart public utility, manufacturing, and transportation accounted for over half of the IoT end users.
- One of the major causes of growing cyberattacks is the lack of skilled cybersecurity personnel in each industry. In China, experienced cybersecurity professionals are less than security professionals, who are required to handle cyber threats for financial institutes, government organizations, and private sector/industrial businesses.
- Large businesses are implementing more data-based AI solutions for security and sales. Cybersecurity experts have turned to geospatial data to shore up the lines of defense. Companies can strengthen emergency management, national intelligence, infrastructure protection, and national defense platforms by implementing geospatial data into pre-existing security systems.
- Many organizations in various countries have switched to remote work environments after COVID-19, including China. The rising cyber-attacks involving malware and ransomware are forcing organizations to adopt cybersecurity solutions. Therefore, the Chinese cybersecurity market is anticipated to experience significant growth as a result of the growing work-from-home trend.
China Cyber Security Market Trends
Cloud Deployment Mode Segment is Expected to Hold Significant Market Share
- The need for cloud-based solutions and subsequent growth in the use of on-demand security services is driven by businesses' growing awareness of the value of saving money and resources by transferring their data to the cloud rather than creating and maintaining new data storage. Due to these advantages, major businesses and SMEs in China adopt cloud-based solutions more frequently.
- The increasing realization among enterprises about the importance of saving money and resources by moving their data to the cloud instead of building and maintaining new data storage drives the demand for cloud-based solutions. Owing to multiple benefits, cloud platforms and ecosystems are anticipated to serve as a launchpad for an explosion in the pace and scale of digital innovation over the next few years.
- As IT provision has shifted from on-premise to outside the boundaries of the business, security has been crucial at every stage of the cloud adoption cycle. SMEs prefer cloud deployment because it frees them up to concentrate on their core skills rather than investing their limited cybersecurity funds in security infrastructure. Furthermore, using public cloud services expands the organization's confidence boundary, making security an essential component of the cloud infrastructure. However, the increasing usage of cloud-based solutions has significantly simplified enterprises' adoption of cybersecurity practices.
- With the increased adoption of cloud services, such as Google Drive, Dropbox, and Microsoft Azure, and with these tools emerging as an integral part of business processes, enterprises must deal with security issues, such as losing control over sensitive data. This gives rise to the increased incorporation of on-demand cybersecurity solutions.
- Cloud-based solutions also benefit from lower capital expenditure requirements, thus making the business much more compelling. Deploying cloud-based services can significantly reduce the Capex requirement as the companies need not invest in hardware components. Cloud solutions also enable better prediction of the cost of an application, and companies do not need to incur as much upfront cost to incorporate the technology. The hardware and IT support savings make cloud-based solutions much more affordable.
- Companies considering moving from on-premise software to a cloud-based solution are primarily checking the potential solutions for their capabilities concerning key security features, including standards compliance, intrusion prevention, and detection.
- A CNNIC survey conducted in June 2023 found that a troubling 20% of internet users in China have been victims of online fraud.
Data Security Offering Segment is Expected to Hold Significant Market Share
- The financial sector has been recognized as a prime adopter of regulatory frameworks to implement adequate information and data security standards. These ensure a reliable provision of products and services, safe data processing by its systems, and responsible use of personal data.
- Data security helps reduce risks associated with protecting sensitive data from threats and helps organizations maintain compliance. The data security platforms provide data risk analytics, data monitoring, protection solutions, and protection of the organization's data from database vulnerability. Governments are tightening the mandates on data security, requiring companies to use cybersecurity solutions. This trend, including the use of antivirus and antispyware software, is expected to create a booming market for cyber solutions in the coming years. Compliance is expected to be the key driver of data loss prevention solutions. However, an enterprise's digital transformation strategies, most notably cloud adoption, Big Data analytics, and IoT enablement are also driving enterprise security teams in the region to adopt these products to identify and classify crucial data throughout the organization and reallocate data security controls primarily based on the criticality of the information.
- As organizations continue to digitize their operations and deal with increasingly complex data protection challenges, investment in effective data security measures will be essential to safeguard sensitive information, maintain regulatory compliance, and protect their reputation.
- As digital transformation accelerates and data protection issues become more complex, organizations must invest in adequate security measures to protect sensitive data, meet regulatory requirements, and save their brand image. Increasing data volumes, changing data protection regulations, and the necessity of customers' related concerns are expected to create robust demand for data security solutions.
- A CNNIC survey conducted in June 2023 found that online fraud is the most common internet security issue faced by internet users in China. Around 38% of respondents encountered prize or lottery-winning scams online.
China Cyber Security Industry Overview
The Chinese cybersecurity market is fragmented, with the presence of major players like Palo Alto Networks, ThreatBook, IBM Corporation, QI-ANXIN Technology Group Inc., and Beijing Chaitin Future Technology Co. Ltd. Players in the market are adopting strategies such as partnerships and acquisitions to enhance their product offerings and gain sustainable competitive advantage. For instance,
- In April 2024, Palo Alto Networks, one of the global cybersecurity leaders, and Google Cloud announced the expansion of their partnership with a ten-figure, multi-year commitment. Palo Alto Networks named Google Cloud its AI and infrastructure provider of choice. Google Cloud has long considered Palo Alto Networks its preferred next-generation firewall (NGFW) provider and the expanded agreement solidified that relationship. The collaboration also underscores the critical importance of platformization fueled by AI to automate and consolidate multiple solutions and deliver near-real-time security resolutions.
- In October 2023, IBM unveiled the evolution of its managed detection and response service offerings with AI technologies, including automatically escalating or closing up to 85% of alerts and accelerating security response timelines for clients.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Force Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Buyers/Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Impact of Macroeconomic Factors on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Phishing and Malware Risks among Businesses
- 5.1.2 Rising Utilization of Cloud-Based Services
- 5.1.3 Rising M2M/IoT Connections Requiring Enhanced Cybersecurity in Businesses
- 5.2 Market Restraints
- 5.2.1 Lack of Cybersecurity Experts and Security Challenges with Modern Devices
- 5.2.2 Budgetary Restrictions faced by Organizations, Low Preparedness, and High Reliance on Traditional Authentication Methods
- 5.3 Market Opportunities
- 5.3.1 Growing Trends in IoT, BYOD, AI, and Machine Learning in Cybersecurity
- 5.3.2 Traditional Antivirus Software Industry Transformation
6 MARKET SEGMENTATION
- 6.1 By Offering
- 6.1.1 Security Type
- 6.1.1.1 Cloud Security
- 6.1.1.2 Data Security
- 6.1.1.3 Identity Access Management
- 6.1.1.4 Network Security
- 6.1.1.5 Consumer Security
- 6.1.1.6 Infrastructure Protection
- 6.1.1.7 Other Types
- 6.1.2 Services
- 6.1.1 Security Type
- 6.2 By Deployment
- 6.2.1 Cloud
- 6.2.2 On-premise
- 6.3 By End User
- 6.3.1 BFSI
- 6.3.2 Healthcare
- 6.3.3 Manufacturing
- 6.3.4 Government & Defense
- 6.3.5 IT and Telecommunication
- 6.3.6 Other End Users
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Palo Alto Networks
- 7.1.2 ThreatBook
- 7.1.3 IBM Corporation
- 7.1.4 QI-ANXIN Technology Group Inc.
- 7.1.5 Beijing Chaitin Future Technology Co. Ltd
- 7.1.6 CoreShield Times
- 7.1.7 River Security
- 7.1.8 Tophant Inc.
- 7.1.9 iJiami
- 7.1.10 IDsManager












